Creating an Incident Response Plan (IRP)
As technology has matured, cybersecurity threats emerging everyday challenge even the best security teams to protect client data, online infrastructure, and systems. Because of this, it's vital for organizations to develop a solid Incident Response Plan (IRP) to allow them to react and remediate all levels of security threats.
What is an Incident Response Plan?
An Incident Response Plan is an organized approach to addressing and managing the impact of a security breach or cyber-attack.
IRPs need to be orderly, systematic, and well thought-out. When a security event occurs, organizations without a plan can go directly into damage control and chaos, and panic might ensue which can compound the problem. IRPs are designed specifically to combat that chaos and panic by giving organizations a structured path to follow. Best-practice IRPs contain documented workflows with step-by-step instructions on how to proceed and who to contact in the event of an incident.
Different IRP approaches will suit different businesses. There isn't a one-size-fits-all recommendation for what your plan should look like. A Managed Security Service Provider (MSSP) could create a detailed IRP that covers every possible type of situation they could encounter, giving their analysts guidance on the best way to respond to various incidents for various types of customers, with the right type of response hinging on their business type and SLA. A small IT shop, on the other hand, might create a high-level IRP that includes a quick step-by-step resolution that can be used to restore business continuity quickly in a variety of situations simply by using backups that have been uploaded to a cloud service provider each day.
Companies with large IT teams should designate a specific team as an Incident Response team, sometimes called a Cybersecurity Incident Response Team (CSIRT), to own the plan and work on the issue, considering it from all facets. A CSIRT should include not only Cybersecurity and IT department team members but also a public communications representative and C-suite members. A diverse yet cohesive team allows for flexibility and a quick, structured remediation.
What's the value of an Incident Response Plan?
Addressing cybersecurity incidents on the fly without a plan can stress teams and put pressure on already-stretched resources. Incident preparedness and having a plan in place to guide you through a problem can reduce the panic that might set in if you are unprepared. Here are three main benefits of creating and maintaining an IRP for use in cybersecurity emergencies:
1. Reduce downtime and MTTR
One of the biggest advantages of following an Incident Response Plan is that it can significantly reduce downtime for your business, and potentially for your customers. A guiding process for teams to use as a path to resolution can be applied to specific incidents or used at a high level, providing key steps that should be followed in a generic fashion.
A well-executed IRP not only reduces downtime but also reduces mean time to remediation (MTTR), which can have a significant impact on company resources. MTTR is important because it’s a powerful predictor of IT incident costs. The higher your IT team’s MTTR, the greater the risk that your organization will experience significant downtime when IT incidents occur, potentially leading to business disruptions, customer dissatisfaction and revenue loss.
2. Save brand reputation and maintain your public trust
IRPs are an excellent way to maintain the hard work and trust that you have created with your customers in the face of a cybersecurity event. For example, quickly recovering data and systems after a Denial of Service (DoS) attack will help show that your company understands the importance of keeping your public-facing web and business services available and reliable for use for your customers.
In the event of a loss of significant data, it can be much more difficult to regain the trust of the public, and potentially significantly damage the reputation of your company. Investing in an IRP is well worth the time and cost for any company and will ensure that your business can quickly respond, remediate, and return to business-as-usual after an incident.
3. Remain in compliance
Remaining in compliance is crucial for many organizations, especially in the healthcare, financial services, and legal verticals. Failure to follow data security protocols can result in substantial fines, loss of business, and trust.
Many businesses cannot afford to take shortcuts or violate compliance regulations. The creation of an IRP helps ensure that your organization follows the rules, best practices, and guidance in your industry. Creating and practicing your IRP helps your business be prepared for a variety of situations that may challenge your abilities to remain in compliance. In this event, following carefully-planned and structured guidance is one of the most effective ways to prepare for a compliance-impacting situation.
Minimizing downtime, maintaining your customers' trust, and remaining in compliance are just a few of the many advantages of having an IRP in place. Whether it’s a cyber-attack or a natural disaster, business-impacting events can happen at any time, so it is critical to have a plan to keep your data protected and help your business recover as quickly as possible.
Do I need an Incident Response Plan?
IRPs used to be an optional safeguard for some types of organizations. However, since strong cybersecurity compliance standards now exist in almost all industries, IRPs are quickly becoming a necessary feature of a well-rounded security plan. For example, the Payment Card Industry Data Security Standard (PCI DSS) requires that complaint entities develop an IRP, test it annually, designate an IRP team, and train employees on how to follow the IRP. But even if compliance standards don’t dictate that your company have or implement an IRP, it’s still worth developing an incident response strategy to ensure that your business is not impacted in other ways.
Breaches cost organizations significant time and money. The longer security events go unremedied, more extensive damage can occur. For public companies, data breaches affect stock evaluation as well as eroding consumer trust and confidence.
All in all, you should consider implementing an IRP if you're interested in optimizing your processes in any of these areas:
- Preparing to deal with incidents
- Identifying and reporting potential security incidents
- Assessing incidents and deciding what action to take
- Responding to incidents by containing, investigating, and resolving them
- Documenting key takeaways and learnings from every incident
How do I create an incident response plan?
When developing an IRP, there are several things to keep in mind:
- You will need to have the support of your leadership and management team. Having this support enables you to assemble the best response team resources.
- Any plan needs to be maintained, tested and updated. Without practice, a team can become unfamiliar with processes and likely make mistakes when a real incident occurs.
- Not every security event is the same, so there is no one-size-fits-all plan. An IRP should outline actionable steps, but also allow for flexibility.
- Reviewing the IRP at least annually and adjusting it based on changing threat landscapes will help ensure you still have the correct resources and tasks in place.
- Designate a chain of command in the event of a security incident. Know which contacts take precedent, whether it be stakeholders, partners, senior management, etc. Each incident may require different skill sets and people to be made aware of the situation.
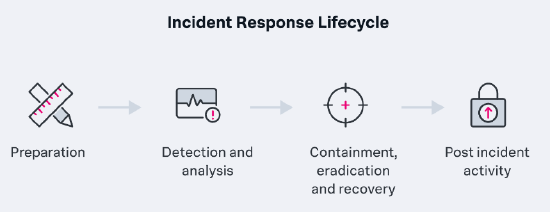
The National Institute of Standards and Technology (NIST) details four phases of the incident response lifecycle. To provide optimal protection and restore service quickly, you should account for all four phases within an IRP:
1. Preparation: The first phase is designed to help organizations determine the risks to their systems and data, outline problem management strategies and put mechanisms in place to deal with security incidents. This can include performing a formal risk assessment, implementing the tools and processes to analyze and mitigate incidents, prioritizing threats, creating,and training an Incident Response Team, and documenting the Incident Response Plan (IRP) in accordance with the NIST lifecycle guidelines.
2. Detection and analysis: In this phase, the service operation sets up systems to proactively monitor, detect, prioritize, and analyze high-priority incidents, with the aim of recognizing any irregular and suspicious threats or activity in the network environment that might disrupt workflow. Detection and analysis are generally done through a combination of human investigation and security tools that automate security processes. With automation and effective execution, this phase can often minimize the spread and impact of an incident.
3. Containment, eradication, and recovery: The third phase addresses security incident resolution. Containment aims to stop the incident from causing further damage - for example, isolating an affected server from the network and implementing firewall rules to block the attacker can stop a malware attack. Security administrators or support staff then remove the threat upon point-of-contact, dispatching the malware from the infected server and making sure it doesn’t exist anywhere else in the system. Finally, support staff recover the system to its state prior to the malware infection and restore service quality by reloading apps or restoring data from backups. The effectiveness of this phase relies heavily on the success of phases one and two.
4. Post-incident activity: Phase four encompasses steps to prevent similar incidents from happening again. Using data collected from the incident and post-mortem meetings, the organization determines how the incident happened, what preventative measures to strengthen or add, how to improve monitoring and alerting processes, and how to streamline service requests, remediation, and recovery processes. You’ll need to address any legal or regulatory compliance issues in this phase as well.
All together, the four phases are designed to build on a comprehensive knowledge base.
Sometimes, organizations focus too much on developing a detailed step-by-step plan of what to do in the event of a breach, but they fail to utilize tools that will make the process easier, such as Splunk SOAR. Even if an organization has the tools, it may be under-utilizing them or using them in the wrong manner. To remedy this, keep a list of tools in use, their renewal dates, and any updates that take place. You should also train employees on how to use those tools, and if no one internally understands the tools well, bring in an expert. Although it may cost more at the outset, proper training could make the difference between an unfortunate breach and a detrimental security event.
An IRP needs three things to be successful: a knowledgeable team who can work from it, an organized plan of attack for the event, and effective tools to aid in investigation and remediation. If an IRP lacks even one of these things, it will likely fail when put to the test.
Next steps
Now you're doing more with Splunk Security Products, get even more value through implementing use cases, or for additional information see some of these great resources:
- .Conf Talk: Splunk® SOAR + SIEM: An automation powerhouse for cyber incident response
- .Conf Talk: Preparing for an industrial cybersecurity incident
- .Conf Talk: Building cyber resiliency through better detection, investigation, and remediation
- Article: What is incident management – security incident response
- Whitepaper: Using Splunk to develop an Incident Response Plan

