Securing infrastructure-as-code with Zscaler Posture Control
Infrastructure as Code (IaC) is widely adopted by organizations to easily deploy, manage, and provision infrastructure in the cloud. Engineers define infrastructure resources using code to consistently scale, update, delete, and provision infrastructure using automation tools.
The focus on speed combined with IaC automation can cause a rapid spread of security issues. For example, an artifact left in an IaC template during development can cause a security gap. A single IaC template misconfiguration might be automatically applied to hundreds, or even thousands, of cloud workloads, amplifying the impact of the misconfiguration. Insecure IaC templates can expand the attack surface and pave ways for critical attack vectors.
You need to integrate security measures into your IaC processes to help prevent these issues.
Required data
- Infrastructure data
- Zscaler data
- Amazon: S3 data
How to use Splunk software for this use case
Security needs to be built-in as part of this high velocity process to provide:
- Continuous monitoring. Security teams can continuously assess risk, speed up reviews, detect violations, and prevent insecure IaC code from reaching production.
- Risk prioritization and alert fatigue elimination. Automatically prioritize risk with rich context so that developers can focus on the violations that are most critical.
- Enriched developer experiences. Guide developers to remediate issues quickly, saving time and resources while keeping pace with new security risks and regulatory compliance changes.
- Visibility. Provide visibility to security, SOC, and development teams on trends of security issues exposed by IaC.
- Reduced cross team friction. Significantly reduce the friction between security and development teams by providing security feedback for developers in the IDE.
A cloud-native application protection platform (CNAPP) significantly increases security by enabling standardization and deeper layered defenses. CNAPP consolidates many of the most important features from siloed point-products into one streamlined platform that comprehensively identifies and helps mitigate cloud risks. CNAPP provides functionality previously implemented by:
- Infrastructure as code
- Cloud security posture management (CSPM)
- Cloud infrastructure entitlement management (CIEM)
- Data protection
- Vulnerability scanning
- Compliance and governance (part of CSPM)
- Cloud workload protection platform (CWPP)
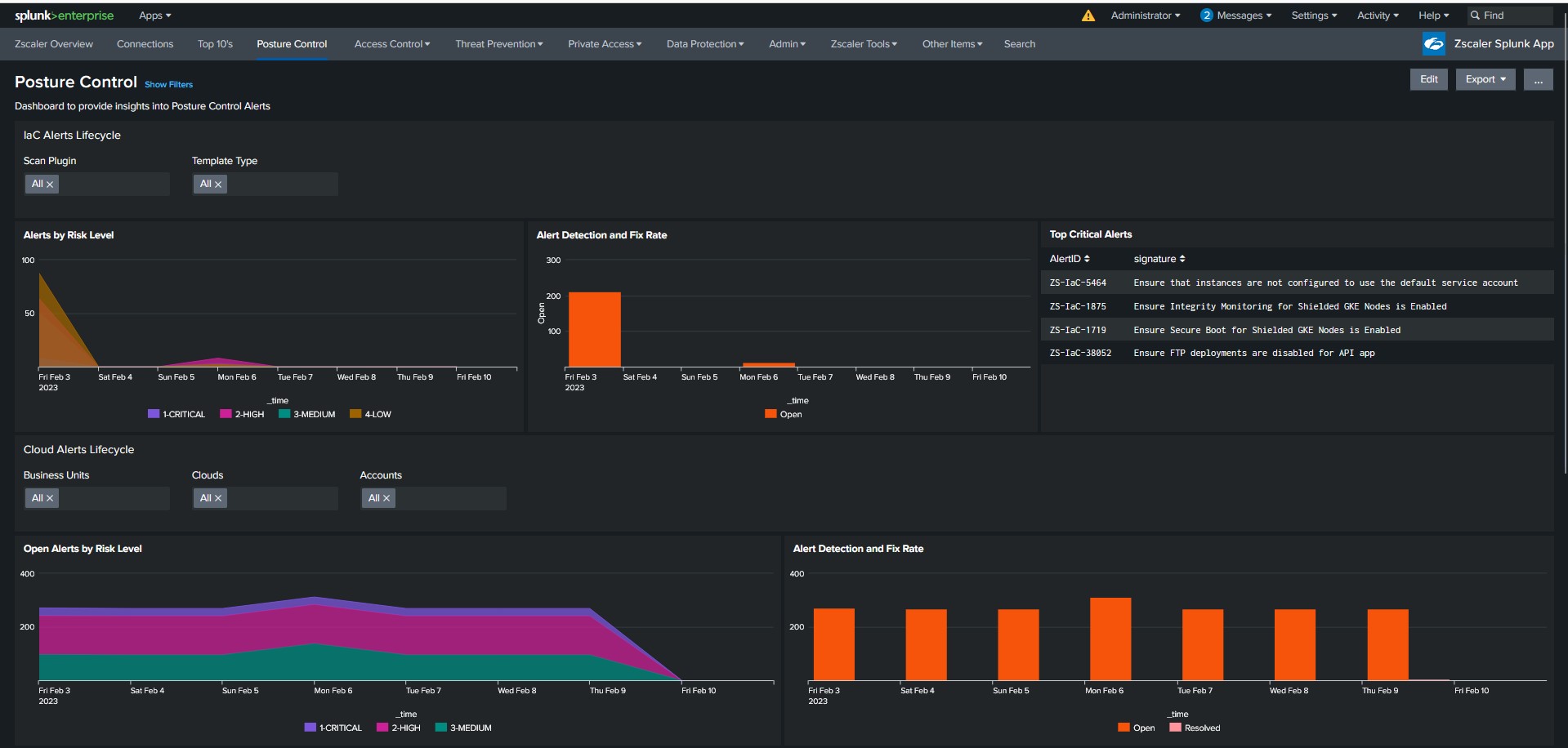
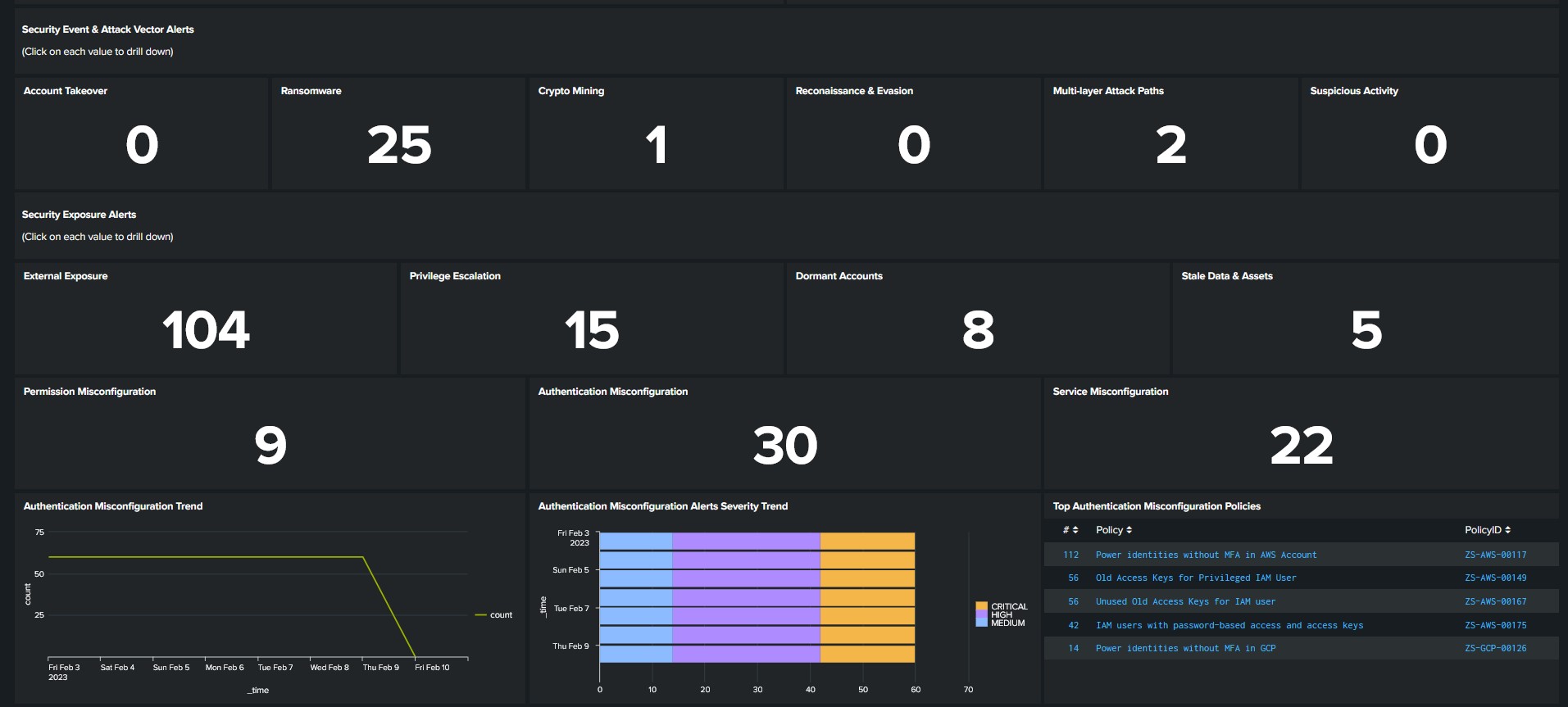
Zscaler Posture Control integration with the Splunk platform provides the SOC valuable insight into IaC vulnerabilities and misconfigurations in cloud infrastructure in a new dashboard within the Zscaler App for Splunk. The new panels include IaC alerts and the top policies that generated them. This is useful for a security team to understand the risks of new templates coming out. Security exposure and attack vectors are also exposed in the dashboard, helping the SOC team identify gaps and threats in a single pane.
Watch the following demo video to learn more.
Next steps
For more information on configuring this integration, see Appendix E: Zscaler Posture Control and Splunk in the Zscaler and Splunk Deployment Guide.
Zscaler accelerates digital transformation so that customers can be more agile, efficient, resilient, and secure. The Posture Control solution is designed to give organizations unified Cloud-Native Application Protection Platform (CNAPP) functionality tailor-made to secure cloud workloads. It enables DevOps and security teams to efficiently prioritize and remediate risks in cloud-native applications earlier in the development lifecycle. The completely agentless solution correlates and prioritizes risks, such as unpatched vulnerabilities in containers and VMs, excessive entitlements and permissions, and cloud service misconfigurations. For more information on how Zscaler Posture Control with Splunk can help protect your organization, contact Zscaler.
The user- and community-generated information, content, data, text, graphics, images, videos, documents and other materials made available on Splunk Lantern is Community Content as provided in the terms and conditions of the Splunk Website Terms of Use, and it should not be implied that Splunk warrants, recommends, endorses or approves of any of the Community Content, nor is Splunk responsible for the availability or accuracy of such. Splunk specifically disclaims any liability and any actions resulting from your use of any information provided on Splunk Lantern.

