Overview - Splunk Intel Management (TruSTAR)
Splunk Intel Management (Legacy) has reached end of sale. If you are an Splunk Enterprise Security customer interested in similar functionality through Splunk Threat Intelligence Management, see the following page: Using Threat Intelligence Management. You can also learn more about the new Splunk Threat Intelligence Management feature here: Assess threats using intelligence data in Splunk Mission Control.
In this short video, you’ll learn about Splunk Intel Management (Legacy), what it is and how it can help your security team.
What is Threat Intelligence?
Threat Intelligence is the collection and contextualization of data that includes indicators, tactics, and techniques in order to perform informed risk based threat detection, mitigation, analysis, and response. Creating and using threat intelligence is a process with action as the end goal. The goal is to produce intelligence that can be cycled back into the process so that an organization’s cybersecurity posture is continually improving.
Creating threat intelligence starts with building blocks of data that are collected, processed and analyzed before they can be made useful. To get threat intelligence, someone or something needs to plow through an immense amount of information in order to sort out what is relevant.
Threat data is generally undefined, and by itself doesn’t indicate if it’s a normal occurrence or a potential threat. Human security analysts are unable to analyze the volume of data generated in a given day and must rely on tools that help organize and present this data in a meaningful way. The process of intelligence begins by putting concrete observables in the data into the context of what we already know or suspect is malicious. Context and interesting observables can certainly come from internal analysis, but more often are learned via intelligence reports. Threat feeds that are populated by private or public entities or communities that dedicate resources to analyzing data and disseminating threat information. Sharing groups that focus on particular industries or verticals, as well as providers like VirusTotal or Crowdstrike, generate information about potential threats on a constant basis. Correlating known observables with the context provided by internal and external intelligence sources can produce indicators of potential threats that should be bubbled up and investigated.
Known threats that have been confirmed can be detected and acted on by your security tools without costly human intervention. The multiplicity of threat feeds can be curated into reports with a threat intelligence management solution.
Threat intelligence is the product of the human analysis of threat information. No automated product can produce threat intelligence. It takes highly skilled human analysts with the security background to review the threat information being produced, make decisions about it based on experience or knowledge, and produce true intelligence that can be reliably acted upon to improve an organization’s cybersecurity program.
Benefits of Threat Intelligence
- Shared knowledge multiplies success
- Identify vulnerable targets quickly
- Confirm and refine Threat Information for your specific environment
- Automate repeatable processes around known threats
- Hunt for new threats, not those already known
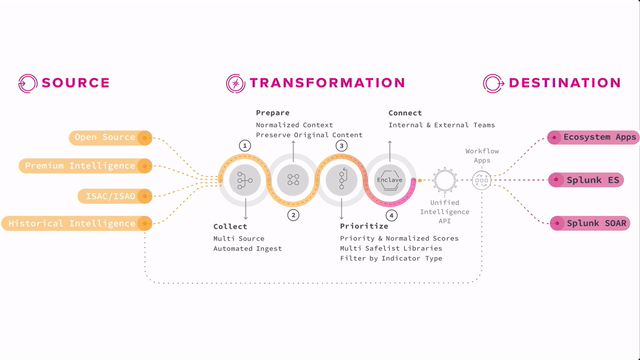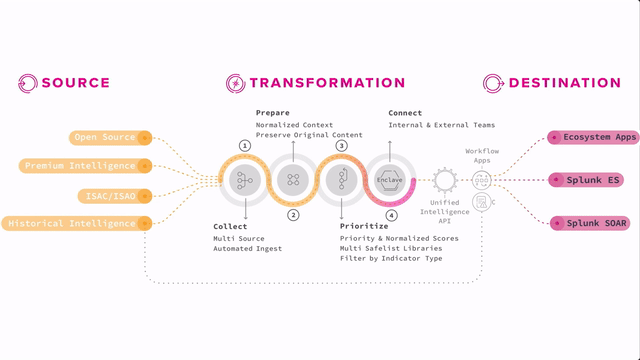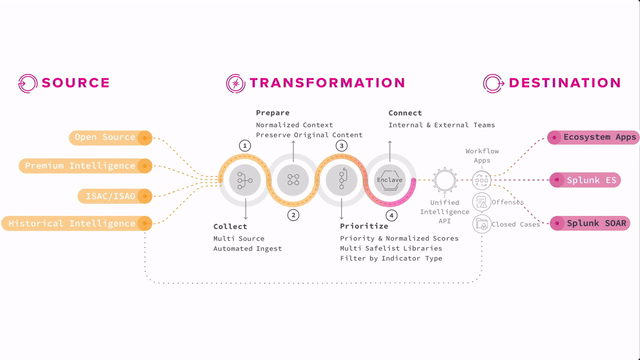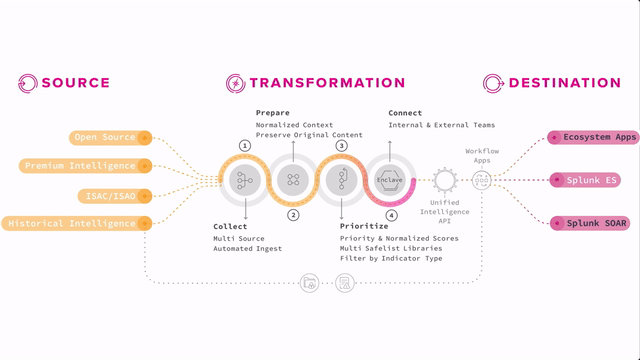
How Splunk Intelligence Management fits into the Splunk Security Suite
Splunk Enterprise Security can ingest this kind of information along with internal data and produce notable events and risk events for analysis. Splunk SOAR can even take action against concrete indicators that have been discovered and put into playbooks.
Think of analysts evaluating notable events from Enterprise Security. If they find a true threat, they might inform the incident response team to take action, add appropriate rules or controls to tools or processes to mitigate the threat in the future, and then use that threat intelligence to refine the rules and searches that produce the notable so that it’s even more accurate or automated for their organization.
Having a threat intelligence program adds that critical human layer that can interact with tools like Splunk Enterprise Security and Splunk Intelligence Management to continually increase effectiveness and thereby improve security posture. That is the point of threat intelligence, to be able to feed that intelligence back into your tools and processes, and back into the community so that you and others can automate and protect against the known threats. And your analysts are free to hunt for the next threats incoming.
Are you a member of the Community Edition?
Watch our welcome video here and learn about the benefits of your membership, or follow the Getting Started path below.