Automating IT remediation with ITSI and Red Hat Ansible
In today’s fast-paced IT environments, organizations strive for maximum uptime and efficiency. It's crucial to ensure digital resilience through preventing, responding to, and quickly recovering from disruptive events. To meet these demands, organizations need integrated solutions that combine the real-time monitoring and analytics capabilities of the Splunk platform with the automation capabilities of Red Hat Ansible Automation Platform.
The combination of Splunk ITSI (ITSI) and the Red Hat Ansible Automation Platform enables organizations to transform reactive troubleshooting into proactive remediation. You can also integrate with Splunk Enterprise Security to enhance threat detection and response as part of your automated IT remediation strategy.
Data required
Red Hat IT operations and security data
About Red Hat Ansible Automation Platform
While the Splunk platform excels at identifying problems and deriving data insights, Red Hat Ansible is an open-source IT automation tool capable of automating remediation steps and orchestrating responses. It simplifies configuration management, application deployment, and orchestration.
Event Driven Ansible, an extension of Ansible, enables users to set up plugins that receive events from the Splunk platform and take action accordingly by implementing conditional logic which examine the event for details about which Ansible playbooks should be run.
The Red Hat Ansible Automation Platform is a unified solution for strategic automation available for enterprise customers as part of the Red Hat subscription. By leveraging Event Driven Ansible and other enterprise-grade components, the Red Hat Ansible Automation Platform combines the security, features, integrations, and flexibility needed to scale automation across domains, orchestrate essential workflows, and optimize IT operations to successfully adopt enterprise AI.
Using the Red Hat Event Driven Ansible Add-on for Splunk
The Red Hat Event Driven Ansible Add-on for Splunk enables Splunk environments to send one or many events at a time to Event Driven Ansible. The add-on is available to download for free from Splunkbase.
After you've downloaded the add-on, to configure the connection from the Splunk platform to Event Driven Ansible, the credentials needed will vary depending on the method for sending data, and the Ansible source plugin used to receive the data.
Webhook
This method involves using the webhook event source plugin on the Ansible side.
- Specify the webhook endpoint configured in the Event Driven Ansible rulebook.
- Toggle SSL Hostname Verification as needed.
- Choose an authentication method (none, basic, or Bearer token).
- Set the connection timeout and retry parameters.

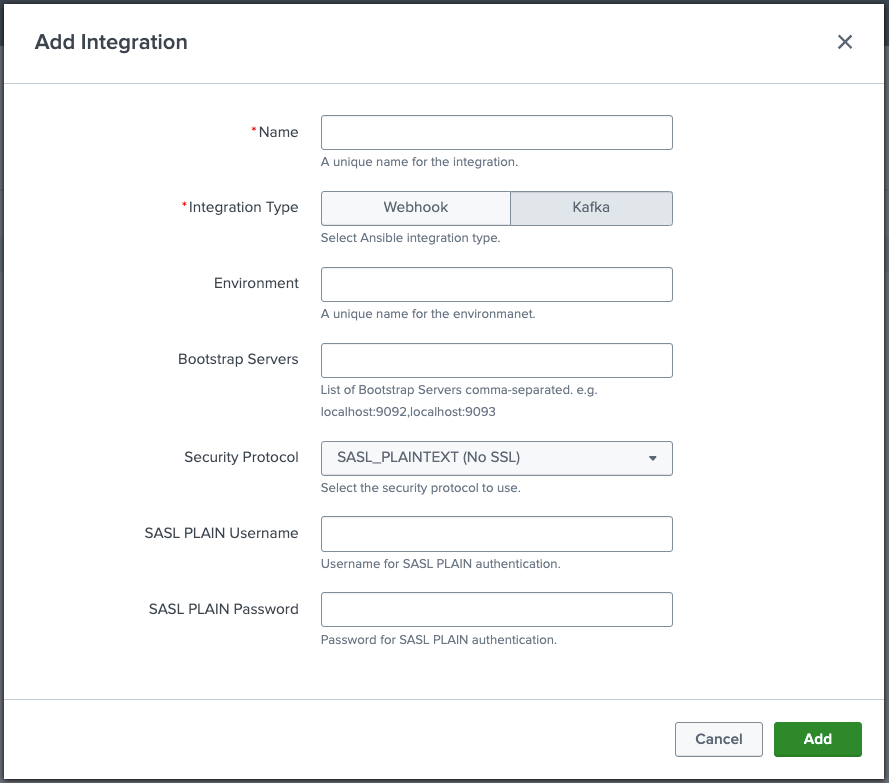
 Kafka
Kafka
To configure Kafka-based communication:
- Set the bootstrap server URL(s).
- Choose the security protocol (None, SASL_PLAINTEXT, or SASL_SSL).
Saved search alert action
The add-on includes a custom alert action that triggers based on a saved search in the Splunk platform. Users can send events to Ansible in one of three ways:
- A single event (default, first row of search results).
- All events in batches (specify results per batch).
- All events in compressed format (gzip compressed payload).

Custom search command
The add-on includes the custom search command kafkapublish, which can send ad-hoc search results to a Kafka environment. Example SPL:
index="main" | kafkapublish topic_name=<> env_name=<>
ITSI custom action
The custom action "Ansible Episode Action (ITSI)" can be run ad-hoc in ITSI on the episode review page or permanently configured as part of the action rules in the ITSI notable events aggregation policy.
In order to invoke the custom Ansible Episode Action from the ITSI episode review page, you must add a stanza to the notable event actions configuration file in the SA-ITOA app local directory. See Splunk Docs for more detailed instructions.
Splunk Enterprise Security action
In Splunk Enterprise Security (ES) you can configure adaptive response actions to automate tasks such as modifying risk scores, adding threat intelligence, running scripts, or sending alerts to Ansible Automation Platform. This is done in the finding-based detection editor.
You can also run adaptive response actions ad hoc from the Incident Review or Mission Control dashboard (depending on ES version) by selecting a notable event and choosing Run Adaptive Response Actions > Ansible Adaptive Response Action (ES) to trigger the sending of notable event details to the Red Hat Ansible Automation Platform.


Next steps
Now that you have the Red Hat Event Driven Ansible Add-on for Splunk running and configured, you will also need to set up your Event Driven Ansible environment with the proper source plugins to receive events from webhooks or Kafka.
In addition, these resources might help you understand and implement this guidance:

