Migrating from Tenable LCE to Splunk Enterprise Security
Tenable Log Correlation Engine (LCE) is a software module that aggregates, normalizes, correlates, and analyzes event log data from many types of devices within an organization's infrastructure. LCE also has the ability to analyze logs for vulnerabilities.
LCE is now no longer supported. However, the Splunk platform, along with Splunk Enterprise Security, can perform all of the same functionality as LCE and more. The Splunk platform log aggregation process, which operates according to the cycle in diagram below, allows for power log analysis capabilities that your analysts can use to secure your organization.

Solution comparison
The information in this article applies to Splunk Enterprise Security (ES) versions 7.x. If you have upgraded to Splunk Enterprise Security version 8.x, some terminology and steps might not apply. For additional assistance on this use case with ES 8.x, Splunk Professional Services can help.
Data ingestion
Just as LCE provides many types of data ingestion methods, so too does the Splunk platform, both on-premises and in the cloud.
| Splunk platform | Tenable LCE |
|---|---|
|
|
Data normalization
After the data is ingested, normalization is critical to being able to search data from a variety of sources.
| Splunk platform | Tenable LCE |
|---|---|
|
The Splunk platform supports all of the common formats and has custom parsing and add-ons which help to transform incoming data to a normalized format. The Splunk platform also supports structured data in the form of data models. It offers the Common Information Model (CIM), a set of field names and tags which are expected to define the least common denominator of a domain of interest. You can use these data models to normalize and validate data at search time, accelerate key data in searches and dashboards, or create new reports and visualizations with Pivot. Using the CIM is critical for getting the most value from Splunk Enterprise Security threat detections. |
LCE supports many log formats, with plugins available to help support more. |
Correlation searches
Correlation rules are searches that can identify a series of events that comprise a larger incident, using common fields, values, or time.
| Splunk platform | Tenable LCE |
|---|---|
Using Splunk Enterprise Security, you can perform a correlation search to scan various data sources, and trigger an adaptive response action. Just as LCE provides automated responses, saved searches and alerts in the Splunk platform can be configured to respond automatically to events. |
LCE provides customizable correlation rules for detecting security threats from log data. |
Search and visualization
| Splunk platform | Tenable LCE |
|---|---|
|
|
File integrity monitoring
| Splunk platform | Tenable LCE |
|---|---|
| The Splunk platform universal forwarder or heavy forwarder supports using OS-based tools such as Windows Audit File System and Linux Auditd. It also offers support for other third-party tools. | The LCE Client can run file integrity monitoring on installed systems. |
How to use Splunk software for this use case
Ready to migrate to Splunk Enterprise Security? Use the following steps to perform the migration on your own, or skip to Next steps to see how to contact Splunk sales for more information.
Prerequisites
LCE version 6 stores data in Postgres database silos. In order to export all historical data, you must have access to the LCE instance and be able to run a few bash commands.
Procedure
- List each silo and its ID.
# source /opt/lce/tools/source-for-psql-shortcuts.sh
# psqlf silos.sql - Dump the logs of each silo to a .txt file, or desired output location/format.
# /opt/lce/tools/rebuild_logs <silo_id> > /tmp/dump_logs.txt
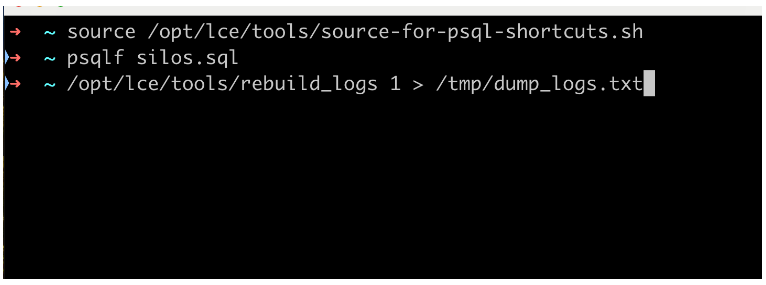
- After this is done, do one of the following:
- Use the universal forwarder to read files and send data in chunks.
- Upload data to the Splunk platform directly:
- In the Settings menu, select Add Data.

- In the "Or get data in with the following methods" section, click Upload files from my computer.

- Upload your log file.

- Set the source type, then click Next.
It might be best to use a source type from the Tenable Add-on for Splunk.

- Configure the parsing for the host field and choose an index to store the data. It's ideal to make a new index. Then click Review.

- Review the information, then click Submit. Your file is uploaded and indexed to the Splunk platform.

- In the Settings menu, select Add Data.
- Replace the LCE client with Splunk platform forwarders. Using the LCE client as an agent to collect data on various endpoints is a crucial method of getting data into your environment. The Splunk platform offers different types of forwarders to meet your specific needs to collect and send data.
Next steps
Contact us at Splunk to learn more about why the Splunk platform, with Splunk Enterprise Security, is the right tool for your log correlation needs.
In addition, the following resources might help you learn more:
- Splunk Help: Overview of the Splunk Common Information Model
- Splunk Help: About the universal forwarder
- Splunk Help: About forwarding and receiving
- Splunk Lantern Article: Getting started with Splunk Enterprise Security

