Generating investigation lists for a virus infection
An event is ingested in your Splunk deployment that indicates a potential virus infection on a server. You want to be able to easily hunt for the virus on other servers and isolate suspect systems.
Solution
The run query action in a Splunk SOAR playbook enables useful investigative tools. In this scenario, you can use run query to discover other servers that have recently connected with the infected server.
- In the Splunk platform, write your search. In this example,
host-001is used as a sample host name for an infected server. Make sure you use the same namespace context in the Splunk platform to test your search as you will use when you connect using the Splunk asset from Splunk SOAR, or set its access control list to have global access.src=host-001 dest=* NOT dest=host-001 | stats count BY dest
- Save the search.
- Test the search by using the savedsearch command to call the saved search on the Splunk platform. In this example, the search is named
mysearchand has a variable host= $server$that has been replaced with the server namewww1.|savedsearch mysearch server="www1"
- Add the search to the playbook in an action block by entering the name of the saved search and filling in any required variables. You can compose and use SPL in this block but calling a saved search on Splunk lets you keep the SPL out of the playbook. This makes maintenance easier on the Splunk server.
- Use a format block to take a common event format (CEF) value (like destinationHostName) and insert it into the search you planned.
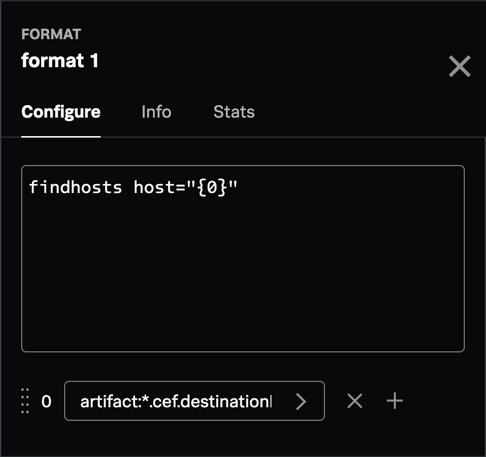
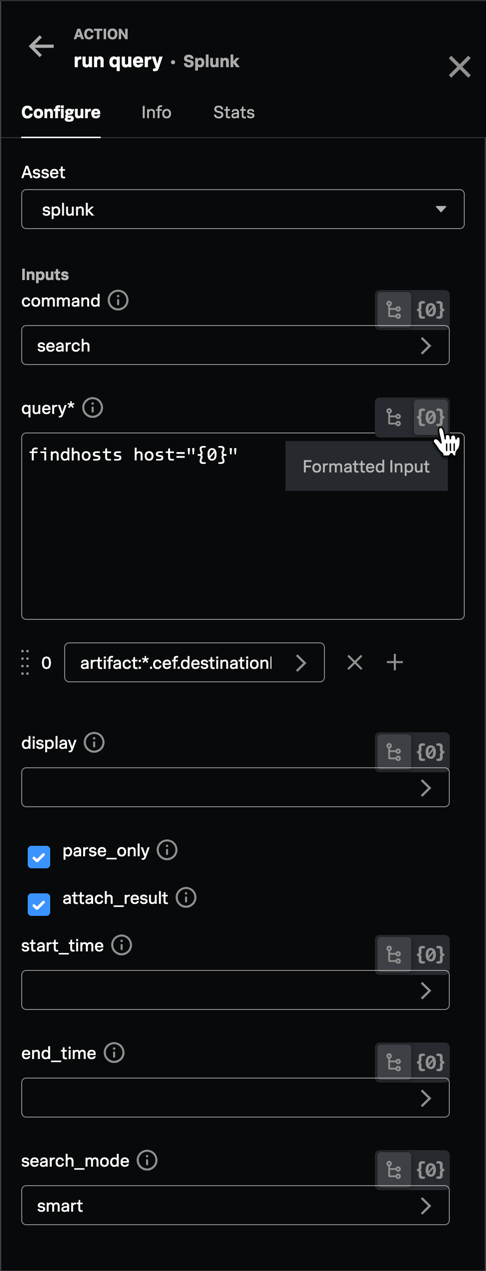
- Configure the following to call the run query action:
- If calling a saved search, use the
savedsearchcommand; otherwise use search to run the query or other command as needed. - Use the Formatted Input option to build a query, or pass in the output of the format block.
- Use the display field to extract a subset of fields to return from the search. This is useful if calling a saved search for which you don't have access to the search definition.
- Select parse_only to test the query without running it.
- Select attach_result to copy the results as a JSON text file to the file vault.
- Fill in the end_time and start_time fields if they are not part of the query.
- In the search_mode field, select one of the following:
- smart (default) returns field extractions for fields used in query
- fast returns only fields listed in display or |fields command
- verbose returns all available fields
- If calling a saved search, use the
Results
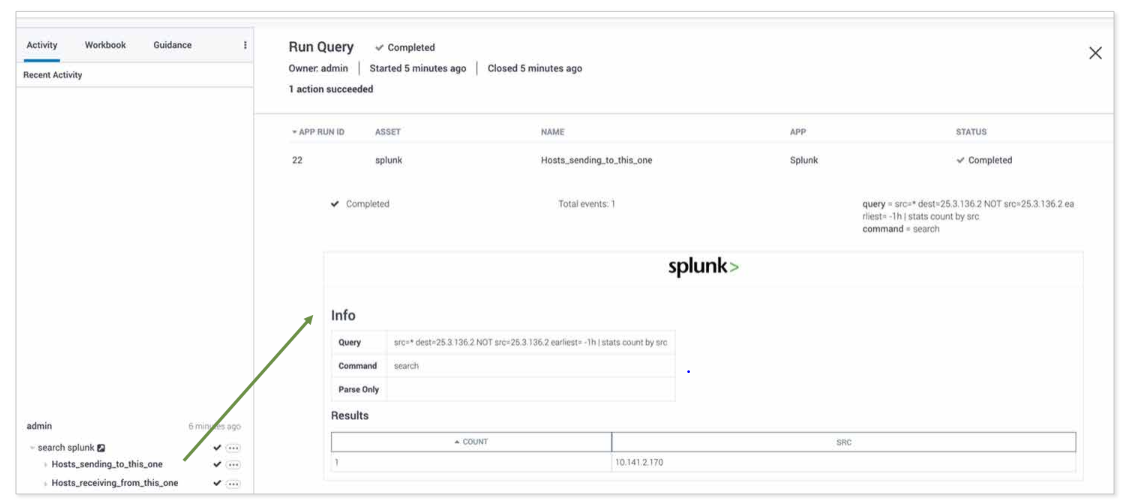
The following screenshot shows sample results from this example playbook. The run query action has returned information on which hosts sent or received data from the infected server in question so you can target your investigation to the right assets.
Next steps
If you found this article useful and want to understand more about the structure of the query action result and how to update the event action, Splunk Education offers a 13.5-hour, instructor-led course on advanced Splunk SOAR implementation. The hands-on labs in the course will teach you how to:
- implement Splunk SOAR solutions
- configure external Splunk searches
- integrate Splunk SOAR into the Splunk platform
- access the Splunk platform from Splunk SOAR
- create custom code
- use the Splunk SOAR REST API
Click here for the course catalog where you can read the details about this and other Splunk SOAR courses, as well as register.

