Auditing with the Splunk App for PCI Compliance
The Payment Card Industry Security Standards Council (PCI SSC) was formed by American Express, Discover, JCB, Visa, and Mastercard on September 7th, 2006 with the goal of managing and evolving the Payment Card Industry Data Security Standard (PCI DSS). The PCI DSS is a set of twelve security requirements that provide a framework for securing cardholder data. Annually, organizations that store, process, or transmit credit card data must undergo a PCI audit to ensure compliance with the PCI DSS.
The PCI audit can be very involved and consume a tremendous amount of man hours gathering evidence in support of the audit. A lot of organizations struggle with staffing constraints, which can impact strategic execution of security plans due to the limitations. You want to leverage your Splunk deployment to make the audit easier.
Required data
How to use Splunk software for this use case
The Splunk App for PCI Compliance is designed to solve the challenges surrounding the PCI audit. This article showcases the Splunk App for PCI Compliance for two specific, audit-related use cases and demonstrates how the app can act as a force multiplier during the PCI audit.
Use Case 1: Requirement 10
The first use case is the PCI DSSv4 requirement 10, which requires organizations to “Log and Monitor all access to System Components and Cardholder Data”. The sub-requirements for this part of PCI are:
- Processes and mechanisms for logging and monitoring all access to system components and cardholder data are defined and documented.
- Audit logs are implemented to support the detection of anomalies and suspicious activity, and the forensic analysis of events.
- Audit logs are protected from destruction and unauthorized modifications.
- Audit logs are reviewed to identify anomalies or suspicious activity.
- Audit log history is retained and available for analysis.
- Time-synchronization mechanisms support consistent time settings across all systems.
- Failures of critical security control systems are detected, reported, and responded to promptly.
The Splunk App for PCI Compliance opens to the Compliance Posture page (Figure 1).
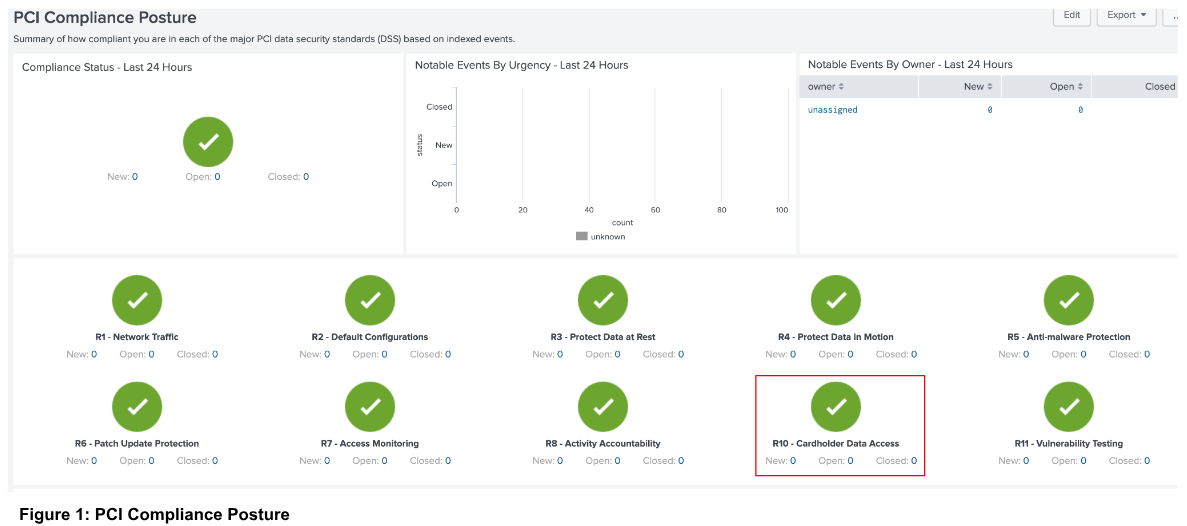
In the bottom pane, click a requirement (in this case R10 - Cardholder Data Access, as shown in Figure 1) to be redirected to the PCI Scorecard for Requirement 10 (shown in Figure 2).
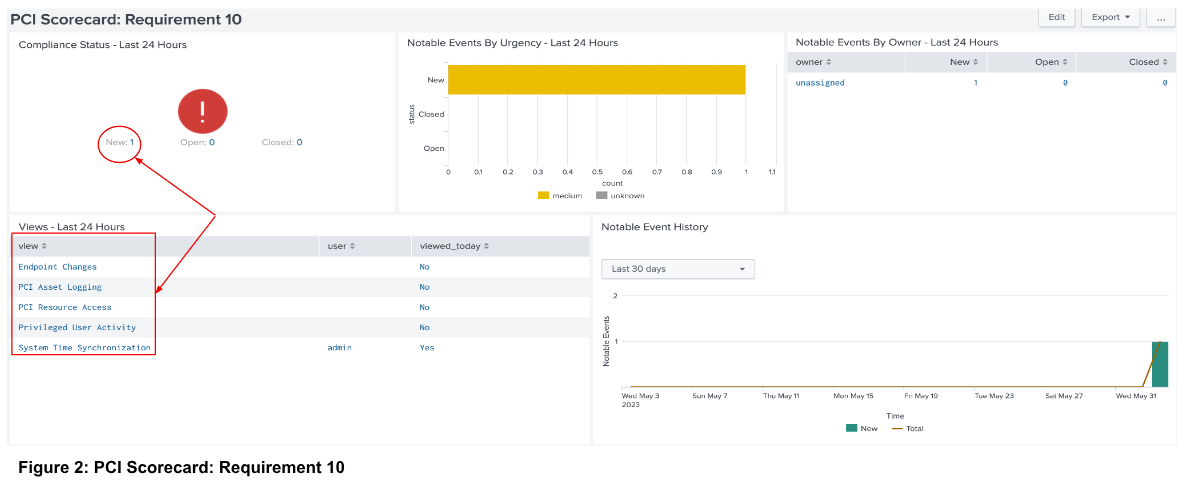
The five links shown within the highlighted box display the sub-requirements with a link to the corresponding reports for each. The table also indicates whether the report has been reviewed. You can also access these reports by navigating to Reports → R10 - Cardholder Data Access and then the desired report. The report displays the assets in the environment and whether the systems should synchronize time.
Click the value in the New field (in this case 1, as shown in Figure 2) in the “Compliance Status - Last 24 Hours” panel to be redirected to the “Incident Review” page. This page displays the non-compliant system for the specific PCI requirement.
Click > to open contextual information surrounding the incident (shown in Figure 3). Context includes a description of the failure and information on the system that failed the PCI requirement. In addition, the contextual information displays both the PCI and MITRE ATT&CK mappings for the PCI deficiency.
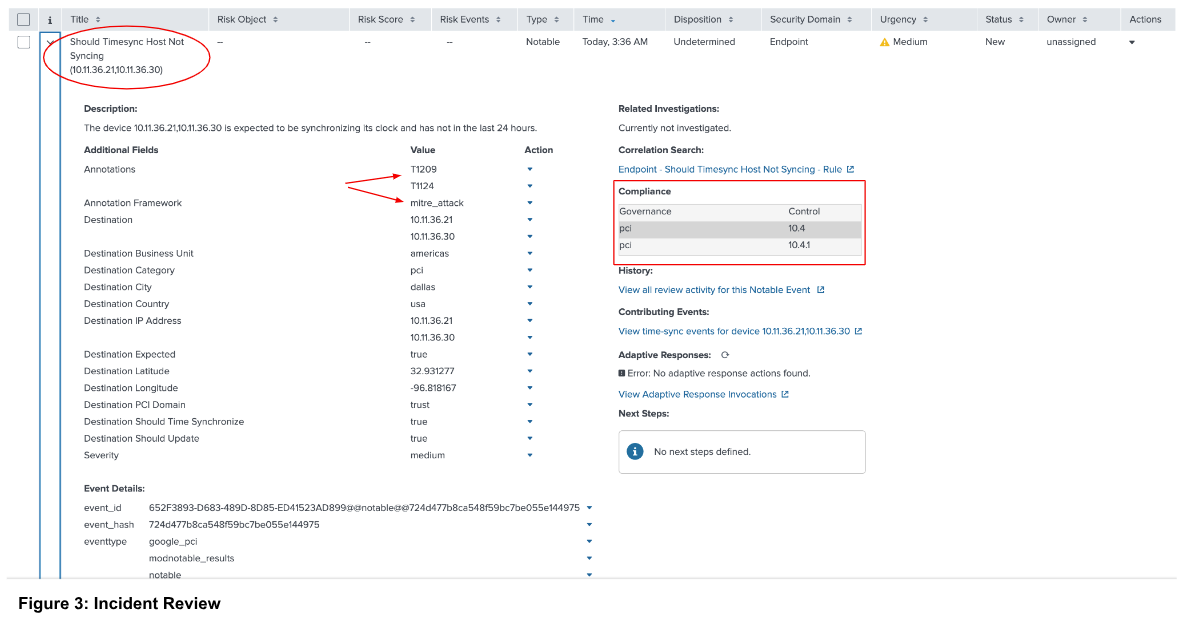
The testing procedure for Requirement 10.4.1 is to “Examine system configuration settings for acquiring, distributing, and storing the correct time to verify the settings are configured in accordance with all elements specified in this requirement.” The Splunk App for PCI Compliance app brings greater efficiency when responding to audit inquiries. Additionally, the app allows you to demonstrate governance over the specific PCI requirement.
Use Case 2: Requirement 5
The second use case is the PCI DSSv4 requirement 5, which requires organizations to “Protect all systems and networks from malicious software”. The sub-requirements are:
- Processes and mechanisms for protecting all systems and networks from malicious software are defined and understood.
- Malicious software (malware) is prevented, or detected and addressed.
- Anti-malware mechanisms and processes are active, maintained, and monitored.
- Anti-phishing mechanisms protect users against phishing attacks.
The intent of requirement 5 is to implement controls so that malware (trojans, bots, ransomware, etc) is blocked or detected and remediated.
Below is the “PCI Scorecard: Requirement 5” page. This page lists four different views and whether the views have been reviewed. Just as in Figure 3, the page also shows the notable events that have been generated and their current status.
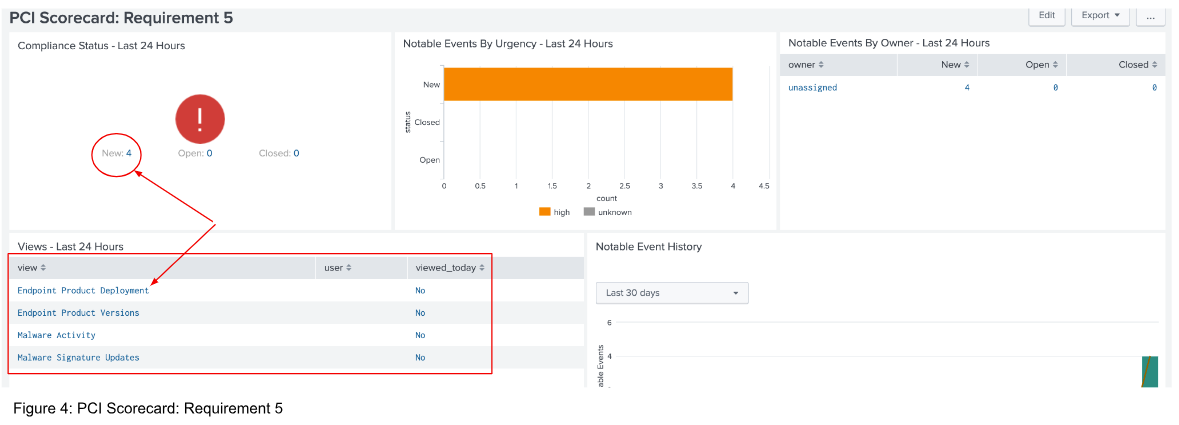
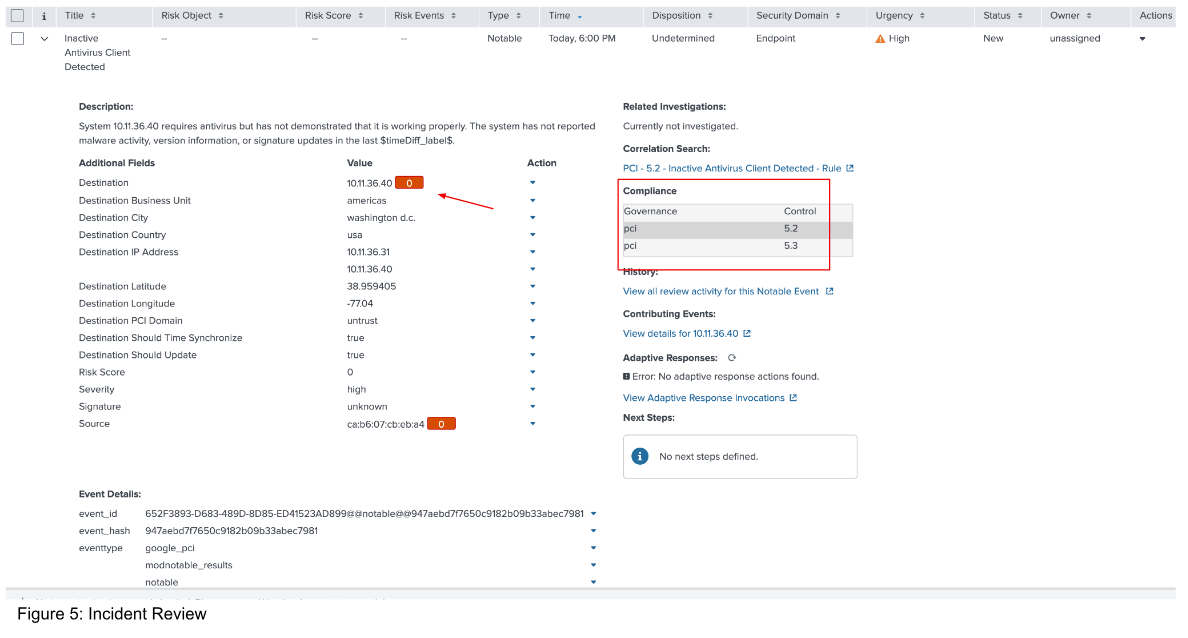
Click the value in the New field (in this case 4, as shown in Figure 4) in the “Compliance Status - Last 24 Hours” panel to be redirected to the “Incident Review” page. There, you can see any Notables, which, in the case of framework compliance, are essentially potential PCI violations detected by the Splunk App for PCI Compliance.
Expand the event to see all the relevant data around the violation. In this case, the violation is due to some type of malfunction with the client’s antivirus agent.
Conclusion
Complying with PCI standards can be a daunting endeavor. The audit process is intense and consumes large numbers of man hours. Manual processes and disjointed reporting and compliance solutions are not sufficient to aid organizations in meeting their PCI objectives. Organizational security data must be present in a centralized cohesive solution to be of meaningful assistance to the governance processes surrounding PCI and other regulatory frameworks. The Splunk platform, along with Splunk Enterprise Security and the Splunk App for PCI Compliance, is uniquely positioned to aid organizations in their PCI efforts.
Next steps
Learn more about Splunk App for PCI Compliance premium app in the user manual to address the requirements for appropriate technical and security controls under the PCI DSS. For additional use cases associated with monitoring and detections that can aid in PCI DSS compliance, read how to get started with security monitoring using Splunk Security Essentials.
Still having trouble? Splunk has many resources available to help get you back on track. We recommend the following:
- Use Case: Using Splunk Enterprise Security to ensure PCI compliance
- Splunk Blog: PCI Compliance done right with Splunk
- Splunk Answers: Ask your question to the Splunk Community, which has provided over 50,000 user solutions to date.
- Splunk Customer Support: Contact Splunk to discuss your environment and receive customer support

