Using threat intelligence in Splunk Enterprise Security
Within an increasingly aggressive threat landscape, security professionals and executives need to explore and implement threat intelligence programs to understand cyber-attacks and remain ahead of the curve. Using threat intelligence data to your advantage is an essential component to any organization’s risk remediation and security program.
Your ability to defend against the modern landscape of dangers such as ransomware, malware, and a multitude of other sophisticated malicious activity is essential in assessing and managing risk. Threat intelligence does exactly that, enabling cyber security teams to inform the security operations center (SOC) and incident response teams of potential and impending harmful activities and business risks.
What’s the value of using threat intelligence with Splunk Enterprise Security?
Threat intelligence can provide huge advantages if it works effectively. Quality threat intelligence goes beyond just providing data-based indicators of compromise you can add to a match list in your SIEM or SOAR platform, it also provides actionable information regarding vulnerabilities, insider threats, leaked credentials and more. Using this information, security teams can reduce the chance of experiencing data breaches and prevent attempts, resulting in measurable savings.
Cybercriminals, fraudulent actors, and malicious insiders alike utilize many tactics, techniques, and procedures (TTP’s) to carry out attacks to reach their end goals (which are often, but not always, to benefit financially). Threat actors are becoming more advanced in their attacks and methods, making it even more important that organizations improve their defense capabilities.
Technical threat intelligence provides the details that enable your security teams to create defense practices and help prevent attacks. With the right data incorporated, cyber security teams can immediately notify appropriate resource owners when they become aware of illicit schemes, such as an insider attempting to sell access to company systems or a threat actor claiming to have collections of the organization's credentials. By investigating and addressing these kinds of situations before they escalate, organizations can make threat intelligence actionable while seeing positive impacts on their ROI.
Where do I get threat intelligence?
Having access to good quality technical intelligence can be tricky since most of the rich data out there isn’t indexed by search engines. Actionable data is often found on multiple mediums, including illicit marketplaces, forums, blogs, social media, and more. This dynamic ocean of data consists of too many sources for most organizations to track and monitor themselves. Additionally, accessing data sources on the deep web and dark web can bring unforeseen risk and exposure to the organization in their attempts to explore and leverage it.
Splunk helps organizations by bringing together threat intelligence sources from across the internet into the Splunk Enterprise Security platform, out of the box and at no extra cost. The threat intelligence sources are parsed for threat indicators and added to the relevant KV Store collections.
The following generic or non-threat intelligence sources are enabled by default:
- Mozilla Public Suffix List
- MITRE ATT&CK Framework
- ICANN Top-level Domains List
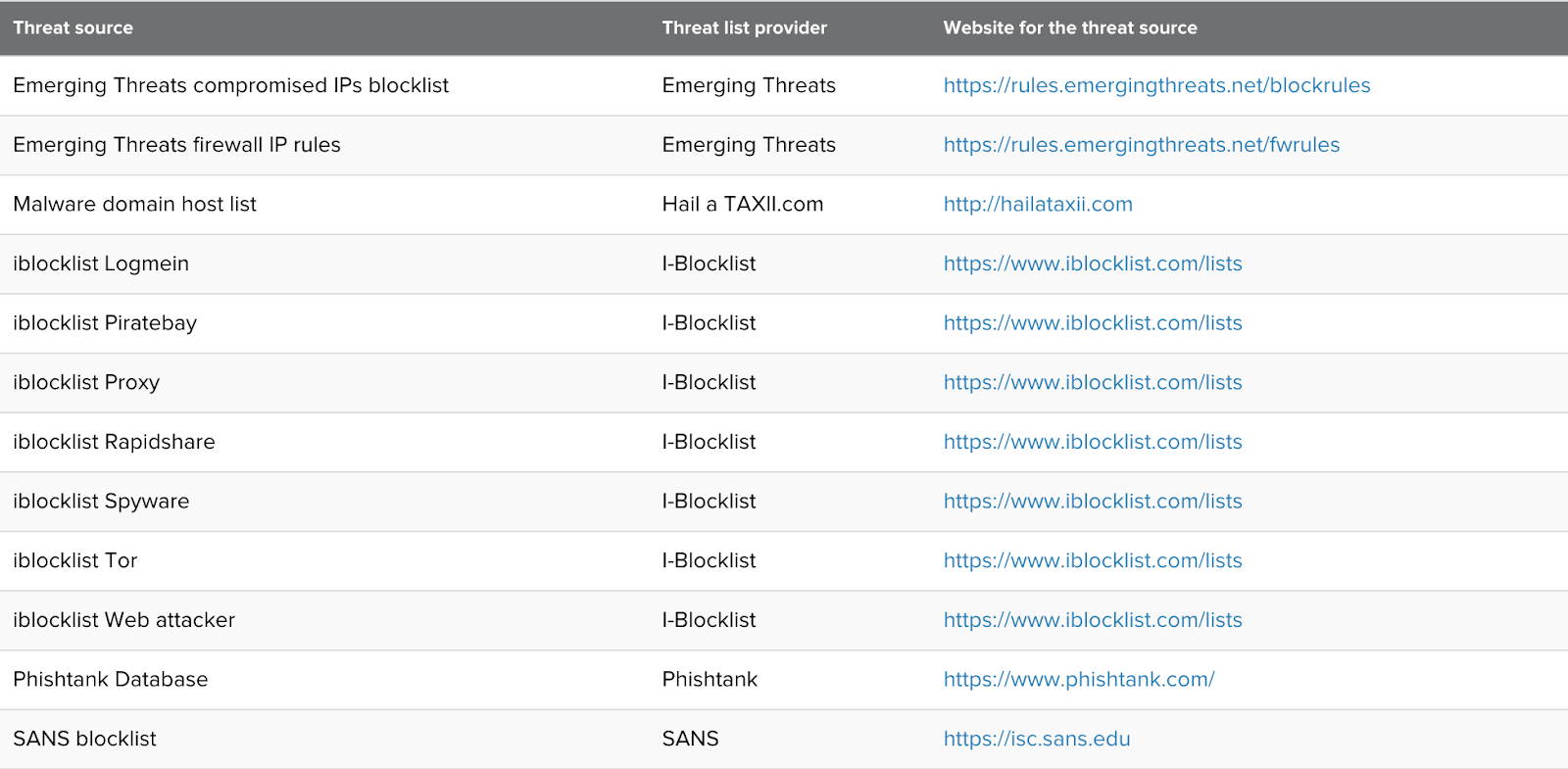
Additionally, several other quality sources of threat data are available and just need to be enabled for use:
How do I start using threat intelligence to my advantage?
Now that you have data, where should your organization start? The threat intelligence gathering process can be cumbersome, resource-intensive, and highly technical, which is why some businesses choose not to incorporate it into their risk-remediation program. Using curated vendor threat intelligence or Splunk’s own threat intelligence management capabilities can help ease you into this complex task.
If done right, even one person can replicate the workflows of a more mature team. One way to have both actionable and scalable threat intelligence is to include this information as part of the correlation search activity performed by Splunk Enterprise Security. Leveraging your threat information to build your search and defense strategies can save you time and resources, and help point your security analysts in the right direction.
If you can build the right foundations, an effective risk-remediation and security program is within your reach.
How to add threat intelligence to Splunk Enterprise Security
The information in this article applies to Splunk Enterprise Security (ES) versions 7.x. If you have upgraded to Splunk Enterprise Security version 8.x, some terminology and steps might not apply. For additional assistance on this use case with ES 8.x, Splunk Professional Services can help.
As an Splunk Enterprise Security administrator, you can correlate indicators of suspicious activity, known threats, or potential threats with your events by adding threat intelligence to your deployment. Adding threat intelligence enhances your analysts' security monitoring capabilities and adds context to their investigations.
Splunk Enterprise Security also supports multiple types of threat intelligence so that you can add your own threat intelligence.
Splunk Enterprise Security administrators can add threat intelligence by downloading a feed from the Internet, uploading a structured file, or inserting the threat intelligence directly from events into your deployment.
Before you get started, you should review the types of threat intelligence that Splunk Enterprise Security supports. See Supported types of threat intelligence in Splunk Enterprise Security.
- Configure the threat intelligence sources included with Splunk Enterprise Security.

- For each additional threat intelligence source not already included with Splunk Enterprise Security, follow the procedure to add threat intelligence that matches the source and format of the intelligence that you want to add:
- Upload a STIX or OpenIOC structured threat intelligence file
- Upload a custom CSV file of threat intelligence
- Add threat intelligence from Splunk events in Splunk Enterprise Security
- Add and maintain threat intelligence locally in Splunk Enterprise Security
- Add threat intelligence with a custom lookup file in Splunk Enterprise Security
- Upload threat intelligence using REST API
- Verify that you have added threat intelligence successfully in Splunk Enterprise Security.

Next steps
These resources might help you understand and implement this guidance:
- Splunk .Conf Talk: Expect more from your threat intelligence in Splunk Enterprise Security and Splunk SOAR
- Splunk Docs: Threat intelligence framework in Splunk ES
- Splunk Docs: Add threat intelligence to Splunk Enterprise[1]

