Enabling Windows event log process command line logging via group policy object
Process command line logging enhances the Windows event ID 4688, providing visibility into any parameters passed through to the process at execution time. This additional context is often required to differentiate between benign process execution events and malicious activity.
The process command line field aligns event ID 4688 to the Endpoint.processes CIM data model, which hundreds of ESCU detections use to detect adversary methodologies, such as living off the land.
In order to follow this process, you'll need to ensure that the audit policy Audit Process Creation is enabled. This policy is required to generate event ID 4688. For the full list of required audit policies, see Configuring Windows security audit policies for Enterprise Security visibility.
Solution
In order to enhance event 4688, you'll need to create or modify a group policy that applies to all domain-joined devices.
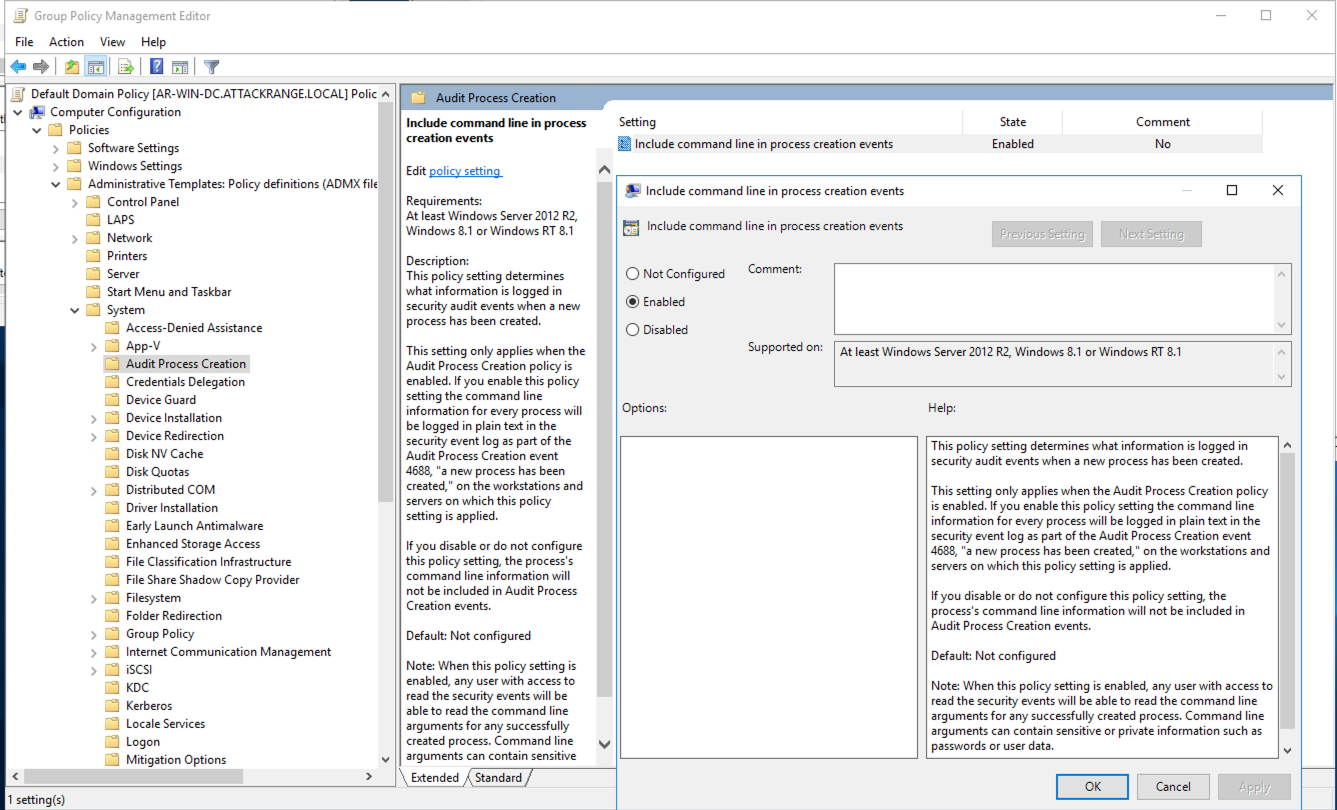
- Navigate to Computer Configuration > Policies > Administrative Templates > System > Audit Process Creation.
- Enable the policy setting named "Include command line in process creation events", and click OK.
After you have done this, you'll see that your 4688 events contain extra context. An example of this can be seen in the image below that shows two 4688 events generated on the same host - one event with command line logging enabled and the other without.
Next steps
These resources might help you understand and implement this guidance:

