Assessing and expanding MITRE ATT&CK coverage in Splunk Enterprise Security
The MITRE ATT&CK framework is widely used in cyber security. It provides a comprehensive understanding of the entire range of threat actors' methods, while including real-world examples. These methods are referred to as tactics and techniques (TTPs).
Because threat actors carefully plan and execute each stage of an attack, it can be challenging for security operators to ensure their defenses are adequate. Using the MITRE ATT&CK framework with Splunk Enterprise Security or Splunk Security Essentials helps you ensure that you have applied security practices across the spectrum of possible attack vectors.
After you've learned the ways that you can get started with using MITRE ATT&CK in Splunk Enterprise Security and Splunk Security Essentials, you'll need to assess and expand your coverage to ensure you don't have any blind spots.
The information in this article applies to Splunk Enterprise Security (ES) versions 7.x. If you have upgraded to Splunk Enterprise Security version 8.x, some terminology and steps might not apply. For additional assistance on this use case with ES 8.x, Splunk Professional Services can help.
MITRE ATT&CK coverage in Splunk Enterprise Security
You can assess coverage and identify defense gaps by mapping your correlation rules against the MITRE ATT&CK framework.
You can use the MITRE ATT&CK Navigator to see the TTPs covered by correlation rules in Splunk Enterprise Security. The heat map in the Navigator uses darker blue colors to indicate a higher number of correlation rules aligned to a TTP.
Within Splunk Enterprise Security, incorporating the MITRE ATT&CK framework can be done easily through enabling out-of-the-box content. When Splunk Enterprise Security is used as a centralized place to gain security visibility and configure alerting, you can work from within it to start assessing gaps in your MITRE ATT&CK coverage. By mapping each Splunk Enterprise Security correlation rule to TTPs, you can learn what detection capabilities exist in your content management set and how current threats in your notable events converge with observed TTPs.
Determining your MITRE ATT&CK coverage
To determine your coverage with the MITRE ATT&CK framework, use the following query to find the percentage of coverage in your current enabled correlation rules:
| rest /services/saved/searches splunk_server=local
| where match('action.correlationsearch.enabled', "1|[Tt]|[Tt][Rr][Uu][Ee]") and match('is_scheduled',"1") and match('disabled',"0")
| eventstats count as total
| search action.correlationsearch.annotations="*mitre*"
| stats count as "mitre" by total
| eval percentage=(mitre*100)/total
| eval percentage=round(percentage,2)
The search will return results that look like this:
.png?revision=1)
From here you'll need to learn the details of the TTPs that are being detected within your rules. There are two ways you can determine this - by searching for tactic and technique coverage or by using visualizations to determine TTP coverage.
Searching for tactic and technique coverage
You can use searches to provide you with the tactic information for any notable that has a detected “mitre attack tactic annotation” field, and how many times that tactic has shown up.
index=notable "annotations.mitre_attack.mitre_tactic"="*" | stats count by "annotations.mitre_attack".mitre_tactic
The same search can be modified and used to detect techniques:
index=notable "annotations.mitre_attack"="*" | stats count by "annotations.mitre_attack"
Using visualizations to determine TTP coverage
Alternatively, you can use Splunk Enterprise Security to visualize the MITRE ATT&CK detections by exploring visualizations on notable events. These visualizations provide you with the observed tactics and techniques for a given asset or identity. Using this information you gain instant context to determine how critical the risk event is, saving valuable time to build situational awareness around a given machine or user. You can also access links to reference material from MITRE, helping you to gather additional information about a tactic or technique and its associated threat actors so that you can effectively plan your response.
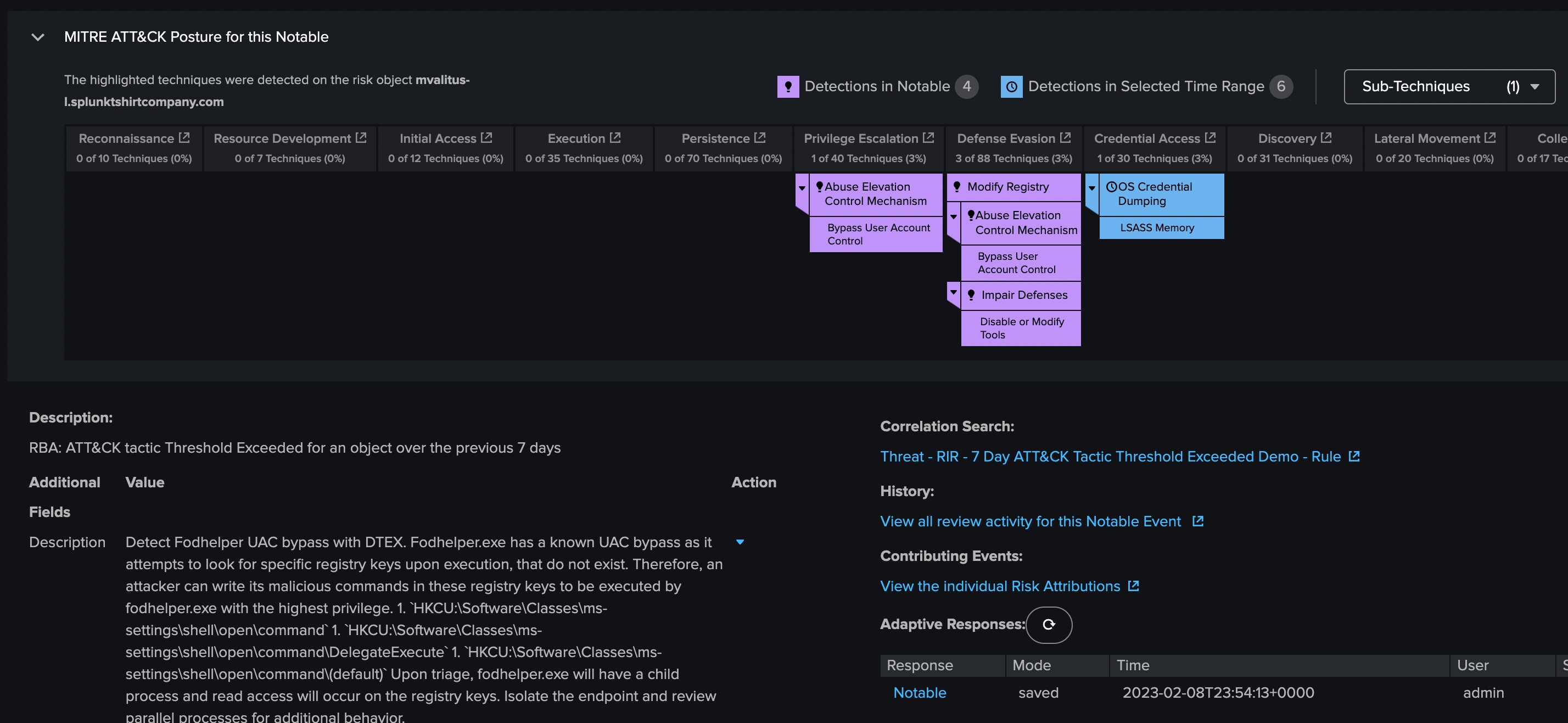
Expanding MITRE ATT&CK coverage
When you understand the detail of your existing MITRE ATT&CK coverage, you'll be in a good place to start expanding and improving your defense and risk posture by enabling new correlations.
Differently-constructed correlation rules can impact how your coverage is measured. For example, if you have several correlation rules in place to detect various types of ransomware, your rules will appear as they are heavily skewed to the MITRE ATT&CK - Impact tactic. However, if you have one rule that detects many types of ransomware, the graphical representation of your MITRE ATT&CK coverage map might seem to show that your coverage isn't sufficient. Both scenarios have the same net effect, and neither approach is right or wrong. It's important for you to understand your coverage at this level of detail so you can make the right decisions about any future roadmap for rule development in Splunk Enterprise Security.
When you have a clear understanding of the types of use cases that you want to enable correlation on, expanding your MITRE ATT&CK coverage is straightforward. You can do this by using out-of-the-box or custom correlation rules, and incorporating security framework annotations in those rules.
Annotations enrich your correlation search results with MITRE ATT&CK mappings. You can also view these annotations as field labels in the Incident Review and Risk Analysis dashboards.
Follow this process to add annotations:
- Select Configure > Content > Content Management.
- Click the title of the correlation search you want to edit. You can use annotations for industry-standard mappings or unmanaged annotations for custom mappings.
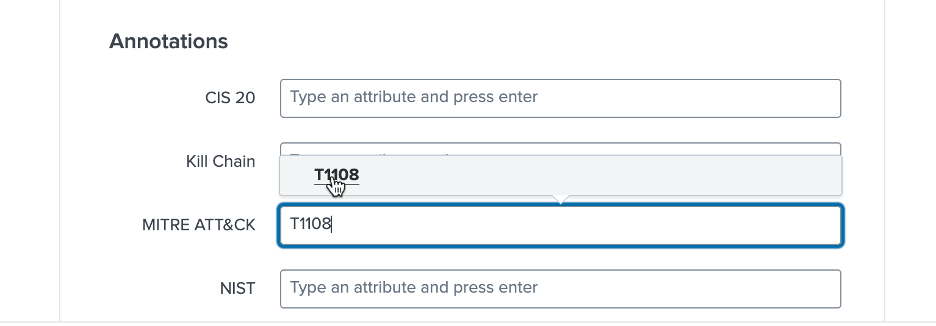
- Provide the MITRE ATT&CK tactic or technique ID in the Annotations field.
Your correlation search should look like this:
.png?revision=1&size=bestfit&width=695)
When filling in the MITRE ATT&CK field, tactic or technique IDs auto-populate as you type them in:
.png?revision=1)
What to expect from using MITRE ATT&CK
Assessing and expanding your MITRE ATT&CK coverage is just one part of using the framework. Another important aspect is establishing a clear expectation of how much coverage it's appropriate and realistic for your organization to achieve.
In the process of setting this expectation, you might want to compare how you have implemented your organization’s coverage to other organizations of similar size and business type. Doing this can provide some value, but it provides little actual benefit in improving your threat detection capability. The internal workings of the organization you're comparing yourself to might differ hugely from yours. You could assume that the other organization has mature processes and detection capabilities, with no way of assessing how valid that assumption is. Even if that organization looks similar to yours, they'll almost certainly have differences in their platform, organizational structure, architecture, or risk posture that makes it difficult to make an apples-to-apples comparison.
Instead, it's more effective to use the MITRE ATT&CK framework to compare your organization to an ideal version of itself. This will provide a customized benchmark that can change as your organization evolves and the threat landscape shifts.
Using cyber frameworks like MITRE ATT&CK is important, but your own unique organizational knowledge and experience is also vital. You should use these frameworks as a guide, while also applying your own critical thinking to the process.
You know the things that keep you up at night, such as a technique that isn't adequately covered, or a concerning technique that you've only been able to cover through layering multiple detection capabilities. By combining your instincts and insights with MITRE ATT&CK and other threat or regulatory frameworks, your organization will be in the best position to defend against threats.
Next steps
These resources might help you understand and implement this guidance:
- Use case: Getting started with using MITRE ATT&CK in Splunk Enterprise Security and Splunk Security Essentials
- .Conf: ATT&CK™ yourself before someone else does
- Blog: Answered: Your most burning questions about planning and operationalizing MITRE ATT&CK
- Docs: Operationalize MITRE ATT&CK
Still having trouble? Splunk has many resources available to help get you back on track. We recommend the following:
- Splunk OnDemand Services: Credit-based services that allow direct access to Splunk technical consultants for a variety of technical services from a pre-defined catalog. Most customers have OnDemand Services per their license support plan. Engage the ODS team at OnDemand-Inquires@splunk.
com if you require assistance. - Splunk Answers: Ask your question to the Splunk Community, which has provided over 50,000 user solutions to date.
- Splunk Customer Support: Contact Splunk to discuss your environment and receive customer support

