Using Splunk SOAR to find gaps in your containment strategy
After we declare an incident and identify a target asset, we must perform further investigative steps. We should not limit our efforts to just the infected asset, but rather, try to gather as much information about it and any other assets that the machine might have come in contact with. Depending on your organization's containment strategy, you might need to divide actions into multiple steps. An asset of interest might be subject to a short-term containment, followed by a detailed evidence collection process, and if necessary it might need to be held back for a much longer containment procedure. This is especially true if the asset in question is where the incident originated from.
Reviewing incidents for opportunities
Splunk SOAR can automate the containment process through the use of playbooks. For example, the risk_notable_auto_containment playbook runs a series of automated actions to assist incident responders. As the playbook runs to identify assets and identities, it runs auto-generated containment playbooks if quarantine actions are required for high threats, as shown in the image below.
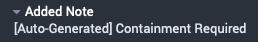
Utility functions create and mark the containment report for evidence as well update Splunk Enterprise Security, as shown in the update Splunk action below.
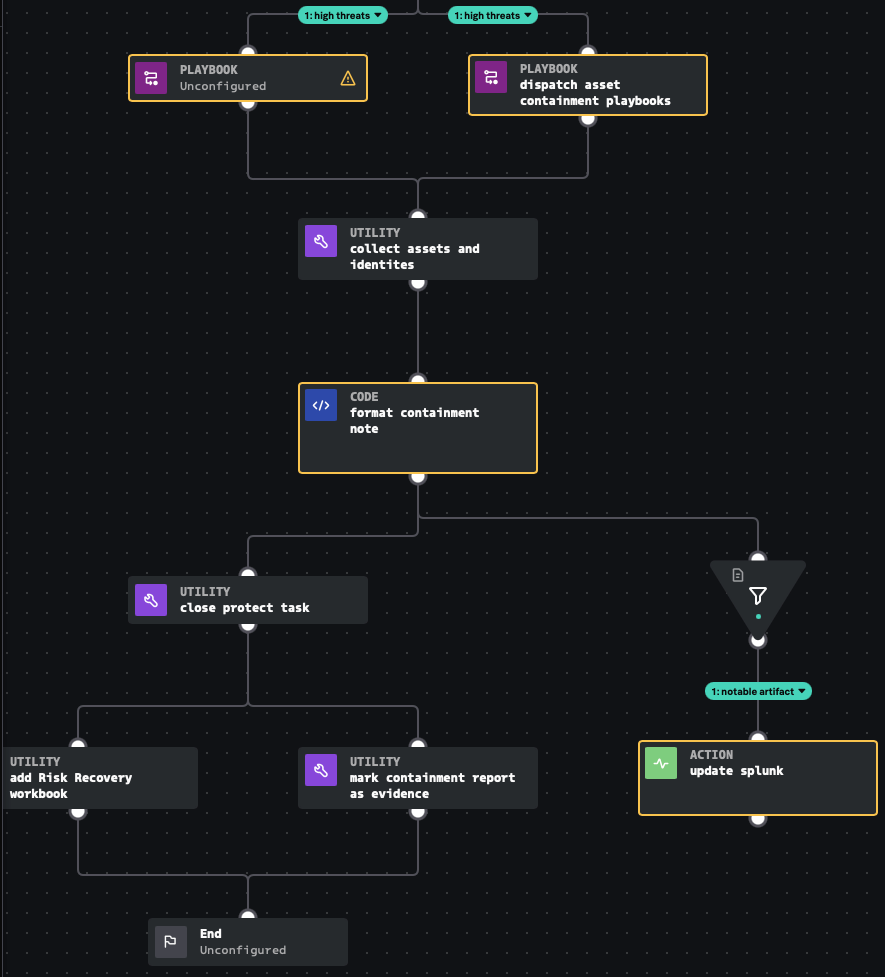
Using the indicator tagging system to your advantage
Before discussing how tags can be used to your advantage, it's important to understand how containers work. All events ingested into SOAR must be stored in a container that also contains all supporting information, known as metadata, for the event. You can use utility blocks in SOAR to set descriptive incident labels that are relevant to your organization. When a playbook runs, it reads the contents of the event's container. This is especially helpful to investigators when reviewing lessons learned because a record of all actions are stored in the playbook's logs. Categories and tags are used to organize playbooks. As a result, if you use descriptive language when developing playbooks, you have created documentation, as shown in the image below.
You can search for tags from the SOAR console to gain additional insights into which playbooks are using the tags you are interested in. When a playbook action or logic block is configured to use a tag, its runtime is based on a tag value. For example, if you are concerned with R&D assets we can configure a tag and assign it to a playbook to see if those assets were involved in an incident.
Response workbooks and post-investigation analysis
After detection rules fire and the correct categorization is applied, the next step is to run the appropriate response workbook. For example, a workbook related to containment would be appropriate in the example above. The intelligence the analyst receives is vital when investigating incidents because a containment workbook contains additional information regarding malicious activity and possible changes to an endpoint's attack surface. The image below shows an example of details about the containment activity.
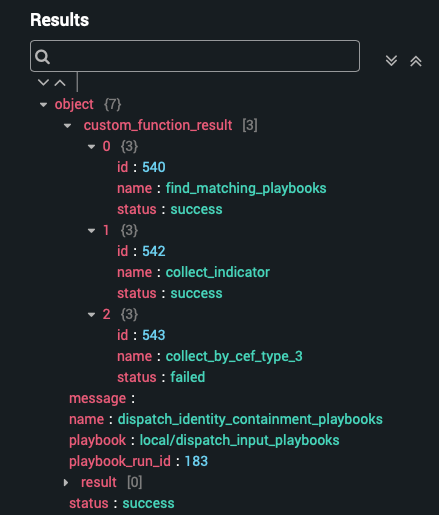
Next steps
These resources might help you understand and implement this guidance:

