Identifying non-defensible networks with Splunk
Having a complete asset and identity network inventory is the first step in creating a defensible network. Knowing which identities are assigned or have access to a particular resource helps cyber defenders and assists incident responders when creating a list of who is supposed to be on the network. This article discusses how to maintain your current inventory and explores techniques to find rogue machines.
The information in this article applies to Splunk Enterprise Security (ES) versions 7.x. If you have upgraded to Splunk Enterprise Security version 8.x, some terminology and steps might not apply. For additional assistance on this use case with ES 8.x, Splunk Professional Services can help.
Taking inventory
There are several ways to find assets and identities in Splunk Enterprise Security. The most popular is by navigating to Security Domains > Identity and then either Asset Center or Identity Center, depending what is being investigated.
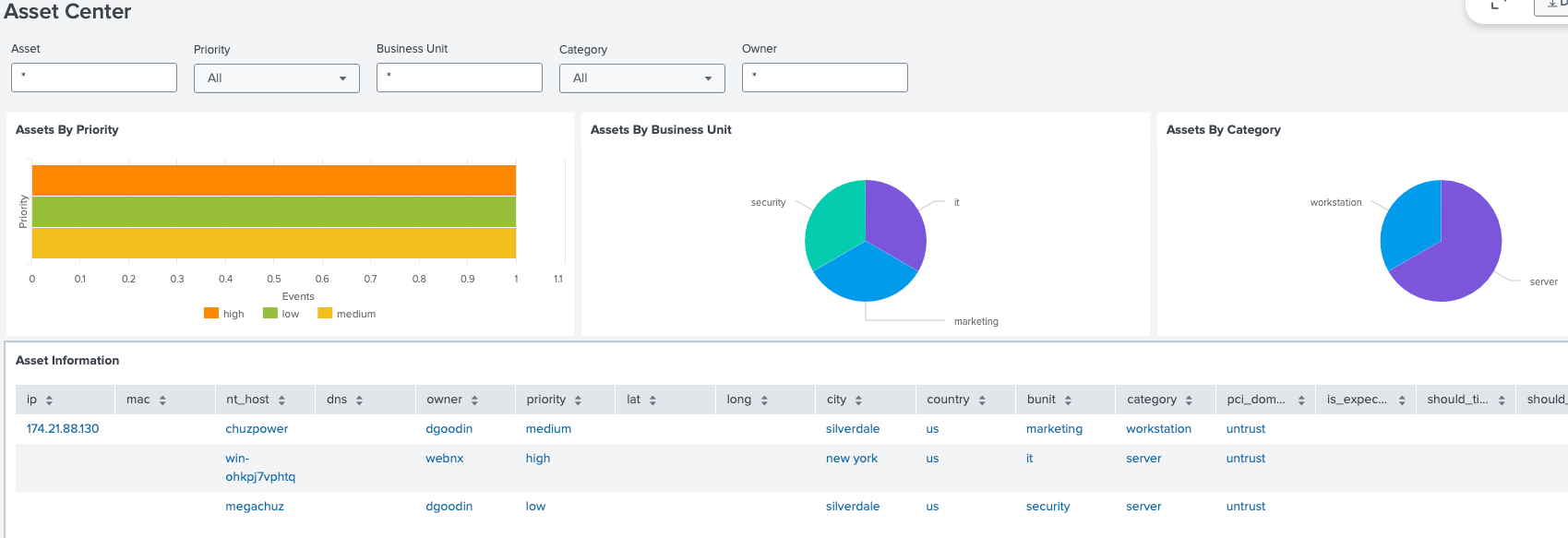
Scanning for success
A common method for finding assets on a network is to scan it. There are many vendor tools that provide scanning capabilities and the more advanced tools provide a traffic analysis to give analysts deeper insights into data. In addition to vendor tools, there are several open source tools such as Network Mapper, also called Nmap, which is widely available across operating systems including Windows, Linux, and macOs. An equivalent tool with a graphical user interface called Zenmap is also available. After those scan results are ingested into Splunk Enterprise Security, IP addresses and, depending on the Nmap scan settings, host information can be processed. The image below shows a typical output of a discovery scan.

Strategies for finding non-standard assets
Depending on your organization's policy for allowing personal hypervisors such as VMware Workstation, Microsoft Hyper-V, and Oracle VM VirtualBox, there may be hundreds, if not thousands, of these unsanctioned machines running at various times. Since every network adapter has a unique identifier known as a MAC address, you can employ advanced network scanning products to search for them. After you find them, you can add these machines to a report for further analysis. An investigator can correlate these results to certain network segments and possibly identify the location in a building or remote location of your organization.
Next steps
These resources might help you understand and implement this guidance:
- Splunk Docs: Collect and extract asset and identity data in Splunk Enterprise Security
- Blog: CMDBs explained: How to maximize value from configuration management databases
- Conf Talk: Blue team academy: Cybersecurity defense analyst
- Conf Talk: Got assets? Detecting & protecting your assets with Splunk
- Tips and Tricks: Correlating Windows and VMware host information
- Use Case: Identifying high-value assets and data sources
- Use Case: Using the Splunk Enterprise Security assets and identities framework

