Using the Splunk App for PCI Compliance
Ensuring data security is more critical than ever for financial organizations. The Payment Card Industry Data Security Standard (PCI DSS) is required for any organization that manages cardholder data. It encompasses twelve primary requirements to safeguard against IT infrastructure data breaches. These organizations must uphold a secure environment crucial for safeguarding cardholder data and preserving consumer trust.
Implementing PCI DSS is one of the most significant hurdles for financial organizations in the payment card industry. However, implementing is only half the battle, as maintaining compliance across the domains requires constant monitoring. The Splunk platform plays a crucial role in automating monitoring activities.
This article provides an introduction to the Splunk App for PCI Compliance, showing you how to use it to monitor and assess PCI DSS requirements while continuously validating technical security controls. If you're familiar with the app and are looking to perform an audit with it, see Auditing with the Splunk App for PCI Compliance. If you're a Splunk Enterprise Security user, see Using Splunk Enterprise Security to ensure PCI compliance.
What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) establishes a comprehensive security framework to protect payment card data throughout its lifecycle. Developed collaboratively by major credit card issuers, the standard mandates specific controls across six primary domains: network security, data protection, vulnerability management, access control, monitoring, and policy development.
Compliance obligations vary according to transaction volume, with organizations categorized into four levels based on annual transaction counts. Level 1 merchants, processing over 6 million transactions annually, face the most stringent requirements, while Level 4 merchants, processing fewer than 20,000 e-commerce transactions, have comparatively modest obligations. This tiered approach ensures that security measures remain proportional to organizational risk profiles while maintaining baseline protection standards across the payment ecosystem, ultimately fostering enhanced data security and stakeholder trust.
How to use the Splunk App for PCI Compliance
The Splunk App for PCI Compliance provides an automated compliance monitoring solution for organizations that manage credit card data. It is compatible with Splunk Enterprise or Splunk Cloud Platform.
The app simplifies compliance management by automatically identifying control gaps, setting remediation priorities, and generating audit documentation on demand. For organizations aiming for constant PCI DSS compliance, this solution turns complex regulations into actionable insights and measurable outcomes, significantly reducing the administrative burden of compliance maintenance and audit preparation.
The app enhances efficiency and practicality in compliance initiatives, and features dashboards that transform how organizations fulfill PCI DSS requirements. Its tools enable comprehensive and clear visibility into compliance status and facilitate promptly identifying threats. This ultimately results in improved protection of cardholder information, and fortifies defenses against data theft loss.
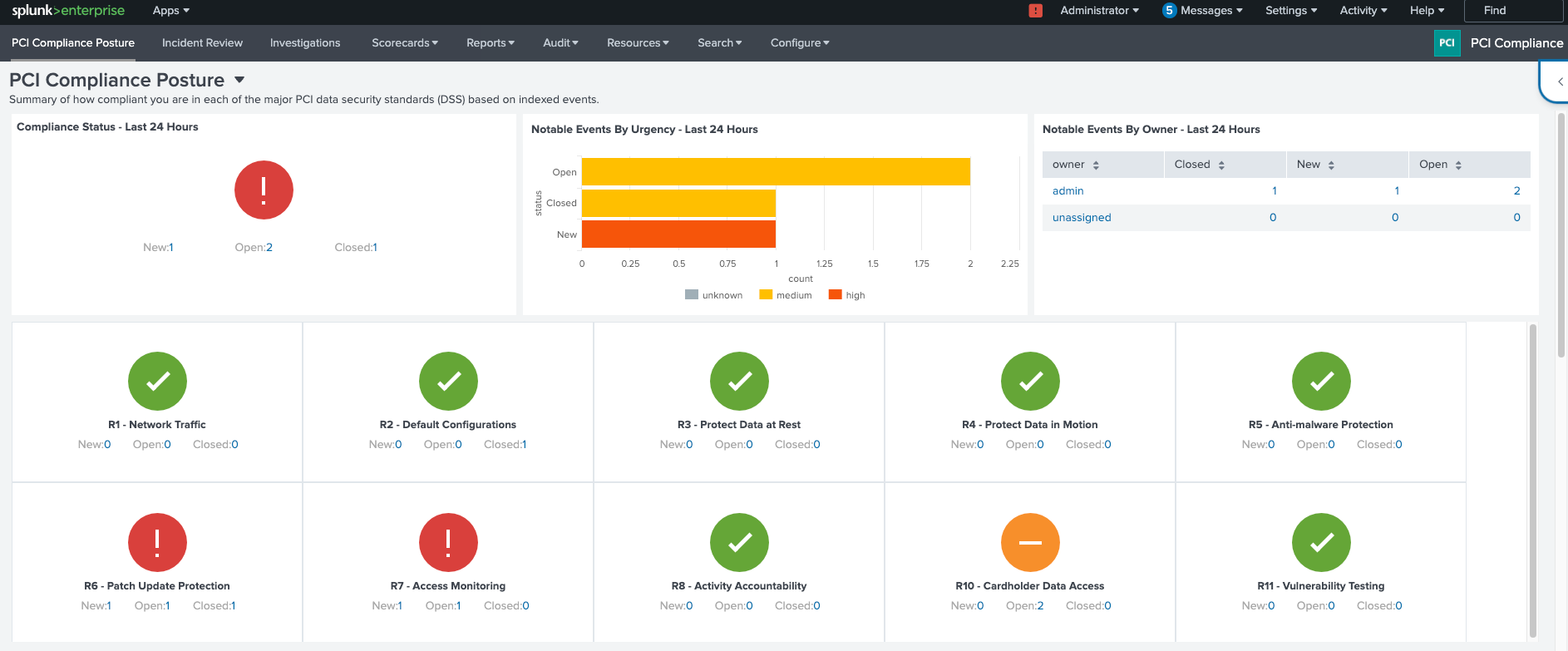
PCI Compliance Posture dashboard
The PCI Compliance Posture dashboard is the monitoring launchpad for compliance teams. It displays real-time security measures and provides color-coded graphs to illustrate compliance across various PCI DSS requirements. As shown in the image below, red signifies new issues, yellow signifies open issues, and green signifies closed issues.
Incident Review dashboard
The Incident Review dashboard manages and analyzes security incidents. It provides an overview of current incidents, including total counts and statuses such as open, in progress, or resolved. Users can access detailed information on each incident, including the incident ID, description, priority, and detection time. The dashboard offers filtering and search capabilities, allowing users to filter incidents by criteria such as date range, severity, or specific compliance requirements. It also includes tools for tracking incident status, enabling teams to update and monitor progress from detection to resolution. Incidents can be assigned to specific team members or groups for further investigation and remediation, ensuring accountability. Additionally, the dashboard provides contextual information and analysis tools to help understand the nature and impact of each incident.
Investigations dashboard
The Investigations dashboard provides tools for conducting thorough analyses of security incidents and compliance issues. From this dashboard, users can manage and document investigations related to PCI DSS compliance by tracking the progress of each investigation and maintaining detailed records of findings and actions taken. It allows team members to collaborate, ensuring that all relevant data and insights are shared efficiently. The dashboard also facilitates the collection of evidence and relevant data, helping to build a comprehensive understanding of each incident. By streamlining the investigation process, the Investigations dashboard ensures incidents are resolved effectively and compliance is maintained.
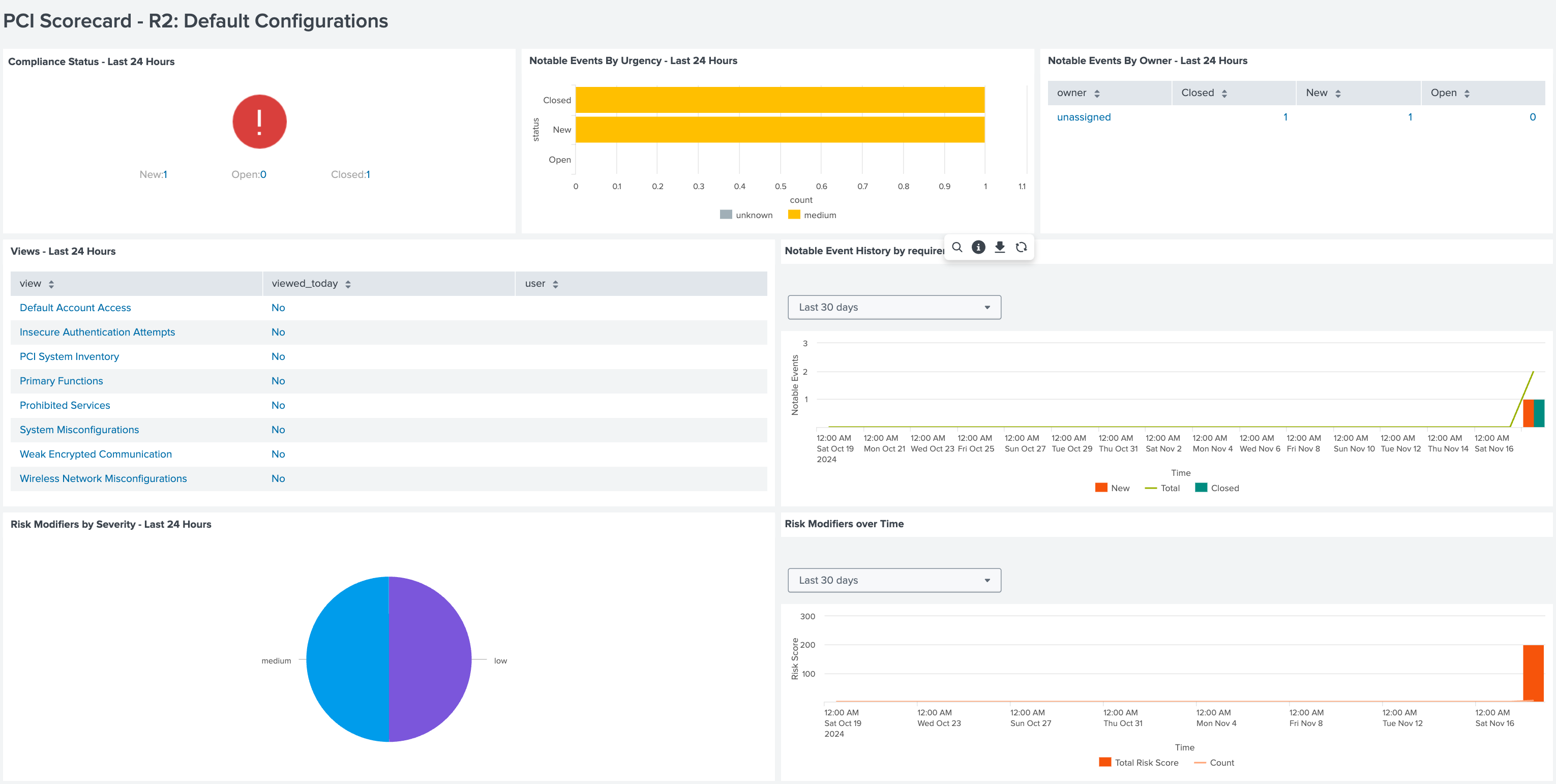
PCI Scorecard dashboard
Scorecards provide a concise view of an organization's compliance status with PCI DSS requirements. The compliance status is displayed by requirement and shows the level of compliance achieved. Scorecards allow analysts to quickly identify compliant areas and those that need attention, facilitating resolution. Scorecards present compliance data in an easily digestible format, assisting organizations in maintaining continuous compliance and preparing for audits. A scorecard for default configurations is shown below.
Reports dashboard
The Splunk App for PCI Compliance features customizable reports which help with audits and regular compliance checks. For instance, an analyst could specify detailed reports on Requirement 2, which focuses on system setups and default accounts. This ensures that every part of compliance is well-documented and easy to track. Reports can also be customized across categories and PCI domains. By default, the following reports are included:
| Requirement | Report |
|---|---|
|
Requirement 1: Network Traffic |
Firewall Rule Activity |
|
Network Traffic Activity |
|
|
Prohibited Services |
|
|
Requirement 2: Default Configuration |
Default Account Access |
|
Insecure Authentication Attempts |
|
|
PCI System Inventory |
|
|
Primary Functions |
|
|
Prohibited Services |
|
|
System Misconfigurations |
|
|
Weak Encrypted Communication |
|
|
Wireless Network Misconfigurations |
|
|
Requirement 3: Protect Data at Rest |
Credit Card Data Found |
|
Requirement 4: Protect Data in Motion
|
Weak Encrypted Communication |
|
Credit Card Data Found |
|
|
Requirement 5: Anti-malware Protection |
Endpoint Product Deployment |
|
Endpoint Product Version |
|
|
Malware Activity |
|
|
Malware Signature Updates |
|
|
Requirement 6: Patch Update Protection |
Anomalous System Update |
|
Default Account Access |
|
|
Update Service Status |
|
|
System Update Status |
|
|
Requirement 7: Access Monitoring |
PCI Command History |
|
PCI Resource Access |
|
|
Requirement 8: Activity Accountability |
Default Account Access |
|
PCI Resource Access |
|
|
Requirement 10: Cardholder Data Access |
Endpoint Changes |
|
PCI Asset Logging |
|
|
PCI Resource Access |
|
|
Privileged User Activity |
|
|
System Time Synchronization |
|
|
PCI Admin Audit |
|
|
Requirement 11: Vulnerability Testing |
Endpoint Changes |
|
Rogue Wireless Access Point Detection |
|
|
Vulnerability Scan Details |
|
|
IDS/IPS Alert Activity |
|
|
Vulnerability Operations |
Audit dashboard
PCI audits require robust and efficient data management to ensure compliance. The Splunk PCI app improves PCI audit performance and protects essential data. Audit dashboards provide the ability to audit different areas and activities in the PCI compliance environment. Audit dashboards are shared with the Splunk Enterprise Security framework. The included audit dashboards are the following:
- Incident Review Audit
- Suppression Audit
- Per-panel Filter Audit
- Threat Intelligence Audit
- ES Configuration Health
- Data Model Audit
- Forwarder Audit
- Indexing Audit
- Search Audit
- View Audit
- Data Protection
Asset Center
The Asset Center manages and monitors assets that fall under PCI DSS compliance requirements. It provides a centralized view of all assets, such as servers, databases, and network devices that are relevant to PCI compliance. The Asset Center enables users to categorize and track these assets, ensuring they are appropriately monitored for compliance-related activities and incidents. It helps identify and maintain an inventory of all assets that store, process, or transmit cardholder data, making it easier to ensure that they meet PCI-DSS standards. Additionally, the Asset Center allows users to associate specific compliance requirements with each asset, facilitating targeted compliance management and reporting. This centralization of asset information supports more efficient compliance monitoring and auditing processes.

Identity Center
The Identity Center manages and monitors user identities and activities to maintain PCI DSS compliance. It provides a centralized view of all user identities interacting with systems processing cardholder data. This feature helps organizations track and monitor user access and activities, ensuring that only authorized individuals can access sensitive information. The Identity Center associates user activities with specific compliance requirements, making identifying and addressing access-related issues easier. By maintaining detailed records of user identities and their interactions, the Identity Center supports auditing. It ensures that access controls are in place and effective, ultimately helping to protect cardholder data and maintain compliance with PCI DSS standards.

Next steps
The Splunk App for PCI Compliance provides businesses with the advanced tools to meet PCI DSS requirements and automate monitoring. As cyber threats change, utilizing the Splunk platform means being ready for any challenge while maintaining compliance.
In addition, these resources might help you understand and implement this guidance:
- Splunk Resource: Splunk PCI App Demo
- Splunk Lantern Article: Using Splunk Enterprise Security to ensure PCI compliance
- Splunk Lantern Article: Auditing with the Splunk App for PCI Compliance
- Splunk Lantern Article: Using Edge Processor to mask or truncate cardholder data for PCI DSS compliance
- Splunk Lantern Article: Using Edge Processor to filter out cardholder data for PCI DSS compliance

