Detecting malicious activities with Sigma rules
As a security analyst, you know that high-fidelity alerts and early detection are essential to minimizing risk of security events impacting your business. There are always new threats, tools, and tactics to watch out for, and threat actors are becoming increasingly more sophisticated. In order to respond, detection tactics also need to become more sophisticated. Using Sigma rules can help you apply these more sophisticated detection tactics.
Why Sigma rules are important for threat detection
Sigma is a useful tool for sharing threat detection information, focused on detecting anomalies in log data such as computer processes, commands, and operations associated with malware or malicious tools. Sigma operates on threat data captured from various sources, while also enabling threat hunters to aggregate events which would otherwise be hard to detect through traditional methods. This means that threat hunters can derive actionable insights from high-fidelity data, and potentially catch an attempted attack earlier in the cyber kill chain.
Sigma is shared in a generic format that is applicable to any type of log file, and needs to be translated to implement into your SIEM tool such as Splunk Enterprise or Splunk Enterprise Security.
Additionally, leveraging Sigma rules supports analysts in moving up the pyramid of pain - from detecting single indicators of compromise (IOCs) contained in network traffic events to specific detections and patterns of behavior. When implemented effectively, Sigma rules can help filter out noise by alerting on multiple parts of a detection versus a single IOC correlation.
Log types supported by Sigma rules include:
- Operating system logs
- Event logs
- Process creation and auditing logs
- Sysmon events
- Web proxy data
- Network VPN data
- Application server data
- Network firewall logs
Sigma rules are great at telling security teams where to look and what to look for. When setting up a detection rule to alert based on these criteria, there is also a lot of information returned for the analyst to use in responding to that detection. If you’re leveraging the Recorded Future App for Splunk with Splunk Enterprise, analysts will also be able to add notes to communicate their findings and what they are working on.
Deploying Sigma rules with the Recorded Future App for Splunk
The Recorded Future App for Splunk enables users to search for and implement Sigma rules written by Recorded Future's threat research team, without leaving your Splunk environment. The team creates detection rules based on current threat research, ensuring they are based on new and emerging threats, including newly released tools and the latest state-sponsored or cybercriminal activity.
The app handles the translation and initial mapping, so that analysts can deploy Sigma rules faster with minimal effort needed. Additionally, users can apply customizations by editing the Splunk search query, and once launched, they can also perform a historical hunt for prior detections.
The app helps users to:
- Identify TTPs for pre-ransomware tools, helping to detect potential threats prior to negative impact.
- Identifying threat actor tactics like lateral movement, reconnaissance, and persistence.
- Detect multi-purpose malware like Qakbot, which is used by threat actors to perform reconnaissance, lateral movement, data exfiltration, and to deliver payloads to infected systems. Sigma rules are used to detect two techniques the malware has been observed to use, including detecting Qakbot defense evasion techniques and registry key modifications.
- Detect the malicious use of malign tools in the reconnaissance and lateral movement stages of an attack, helping to identify the techniques that adversaries use to gain access to a network to dump credentials, escalate privileges, and move laterally.
- Detect malicious behaviors associated with ransomware, such as deletion of Windows shadow copies. This is a common tactic used to ensure data is not easily recoverable by the target in the ransomware enablement phase.
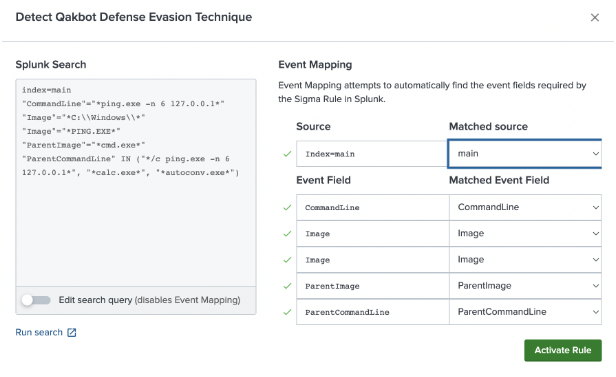
There are many benefits to using Sigma rules inside your Splunk environment, including helping you to be more proactive, detect threats earlier in the cyber kill chain, identify new logging sources needed, improve detection capabilities, and save time. The Recorded Future App for Splunk makes it easier for advanced capabilities to be accessible for all users by leveraging pre-created rules, skipping the translation process, and providing analysts with higher value detections and actionable queries.
Next steps
The following resources will help you get started with the Recorded Future App for Splunk:
- 30-day free trial of The Recorded Future App for Splunk
Recorded Future is the world’s largest intelligence company. Recorded Future’s Intelligence Cloud provides complete coverage across adversaries, infrastructure, and targets. By combining persistent and pervasive automated data collection and analytics with human analysis, Recorded Future provides real-time visibility into the vast digital landscape. It empowers countries and organizations to take proactive action to disrupt adversaries and keep their people, systems, and infrastructure safe. Headquartered in Boston with offices and employees around the world, Recorded Future works with more than 1,500 businesses and government organizations across more than 60 countries. Learn more at recordedfuture.com.
The user- and community-generated information, content, data, text, graphics, images, videos, documents and other materials made available on Splunk Lantern is Community Content as provided in the terms and conditions of the Splunk Website Terms of Use, and it should not be implied that Splunk warrants, recommends, endorses or approves of any of the Community Content, nor is Splunk responsible for the availability or accuracy of such. Splunk specifically disclaims any liability and any actions resulting from your use of any information provided on Splunk Lantern.

