Getting started with Splunk Security Essentials
Key features
Splunk Security Essentials (SSE) provides out-of-the-box security use cases and actionable security content to begin addressing threats and assessing gaps quickly and efficiently. You can leverage the wide-ranging use case library to eliminate gaps in defensive posture, implement detections, and measure and justify new sources of data based on coverage of threats and risks to the business. Additionally, the deep integration with MITRE ATT&CK and Cyber Kill chain helps you configure Splunk Enterprise Security by pushing attributions to the Incident Review Dashboard, assess the level of coverage to ATT&CK tactics and techniques, and integrate risk-based events and alerting.
- Security content library
- Browse, bookmark, and deploy over 900 security detections with a few clicks.
- Find the right security content by filtering via use case, threat, data source, or cybersecurity framework.
- Stay ahead of threats with content that pulls the latest detections from Splunk Threat Research Team.
- Cybersecurity frameworks
- Automatically map your data to cybersecurity frameworks such as MITRE ATT&CK and Cyber Kill Chain.
- Measure your business posture against the frameworks and easily identify gaps to strengthen your defenses.
- Drill down on MITRE tactics, techniques, and threat groups to understand what detections are tied to different phases of the Kill Chain.
- Data and content introspection
- Inspect and analyze data and security content already in your environment.
- Gain a better understanding of your Splunk environment, as well as how your data is or can be Common Information Model (CIM) compliant.
- Enrich your existing security content with tags and metadata such as threat and data source categories, MITRE ATT&CK notes, and more.
- Security Data Journey
- Develop a maturity roadmap with security and data recommendations.
- Track and measure your progress through the Security Data Journey.
- Implement best practices and detections with the data you’re already collecting.
- Prioritize ingestion of new data sources to increase coverage and reduce risks.
In addition, you can curate your own content library by using the bookmarks feature in SSE. You can build a repository of security content for planning, know if you have data missing to make the content effective, track its implementation status, and export content in a variety of methods to easily integrate into another Splunk environment.

Benefits of implementing SSE and using security content use cases
Splunk Security Essentials is an extensive security content library that provides detailed guidance on why and how to expand your security use case content in the Splunk platform, Splunk Enterprise Security, Splunk User Behavior Analytics, and Splunk SOAR environments. SSE uses standard search SPL combined with data prerequisites to help you determine if a use case has the right data in place to gain the most value from the content you are interested in. Implementing an SSE use case requires three steps:
- Validate that you have the right data onboarded and that the fields you want to monitor are properly extracted.
- Verify that the data format (or a lookup, if appropriate) is accurate so that you are just looking at items of focus.
- Save or schedule the search.
The components that make SSE so valuable to use case expansion are:
- Use case and categorization. Select from predefined security use cases and go granular through specific threat categorization.
- Data availability. Understand the data you have and its quality or the data you need to add value to your security operations.
- Cyber framework attribution. Enhance your data with MITRE tactics and techniques and Cyber Kill Chain phases.
- Search results and SPL. Understand what is occurring under the hood with line-by-line SPL documentation.
- Visualizations. Analysts use dashboards and heatmaps to assess posture and identify gaps in threat coverage.
- Introspection. Examine your current saved searches, determine detection alignment to SSE content, or create custom detections.
Splunk Security Essentials content and native detections can be sourced from the collection of out-of-the-box searches, or you can create your own custom saved searches to build your own library to utilize SSE as a content catalog.
How to implement Splunk Security Essentials and use Security Content use cases
Locate and review use cases from the Security Content page
The Security Content page is the main landing page for Splunk Security Essentials. From this page you can easily get a complete list of content or dive deeper into any individual item using a variety of filters. Let’s explore some of the items in Stage 1 of the security journey.
- From the main menu in Splunk Security Essentials, navigate to the Security Content page.
- Navigate to Monitoring and Detection as your starting point. SSE has nearly 120 detection searches in Stage 1.
- Click a detection search to learn how it can help you. For example, clicking on the detection search Basic Brute Force Detection drills into the context so you can understand the impact of the search, learn how it works, adapt it to your environment, and handle the alerts that will be generated by this event. In the content details, you can see the following information:
- Data source links. Click these links to see several popular technologies, not just a list of technologies that provide those data sources. You can also find the installation documentation here.
- Related Splunk capabilities, known false positives, how to respond. Each of these elements help you learn how to implement and respond to these searches.
- Enable SPL mode. By toggling on SPL mode you can see the prerequisite checks that make sure you have the right data onboarded, access the Open in Search buttons, and schedule the saved search right from the app. In case your environment isn't fully compliant for this, SSE provides guidance on how to address it.
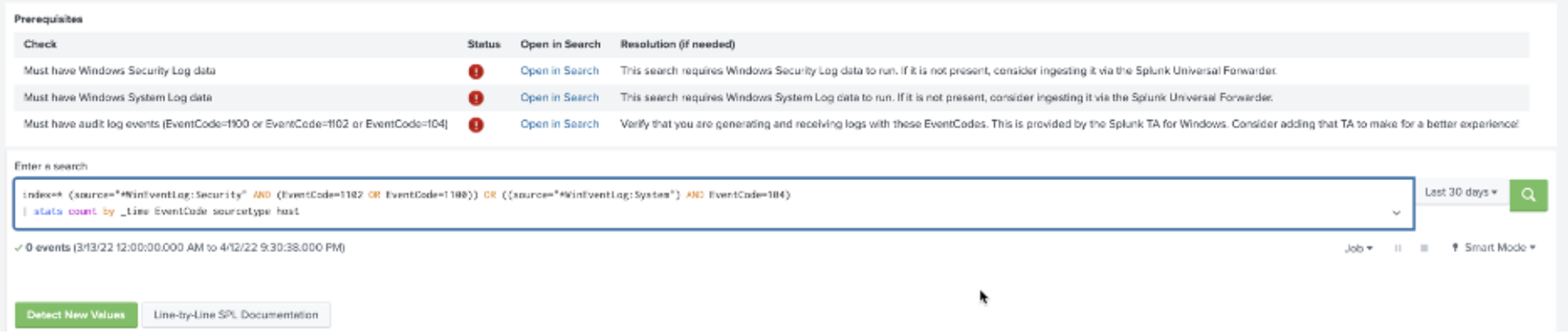
- Click Line-by-Line SPL Documentation link to bring up a commented section. This helps you understand what the SPL does and what is happening upon execution of your use case.
- Click on the View SPL link to access the View buttons, which shows a list of what searches are available for each security content search.

- You can also open the How to Respond section, which helps you understand why this use case is being detected and what you can do to help ensure correct identification and handling.

Understand the data you have and let Splunk Security Essentials guide you to valuable content
You can use SSE to take advantage of the work you have already done in your environment and configure the products that are implemented with the Data Inventory Dashboard.
The Data Inventory dashboard is used to configure the products you have in your environment. Products have a variety of metadata such as source types, event volume, and Common Information Model (CIM) compliance, and are connected with data source categories. The Data Inventory dashboard can show you what content can be turned on using your current data.
To use the Data Inventory dashboard, follow these steps:
- Navigate to Data > Data Inventory.
- From the pop-up window, select one of the following ways to get your data into this dashboard.
- Launch Automated Introspection. If Splunk Security Essentials is installed on your production search head, click Launch Automated Introspection to automatically import data. Introspection allows Splunk Security Essentials to see what data you have available to use across the app.
If you choose Automated Introspection, click Automated Introspection to see the five automated introspection steps that pull in a variety of data.
- Manually Configure. Click Manually Configure to manually enter your data.
- Launch Automated Introspection. If Splunk Security Essentials is installed on your production search head, click Launch Automated Introspection to automatically import data. Introspection allows Splunk Security Essentials to see what data you have available to use across the app.
- If any of your sources or source types don't appear correctly, click Update in the Actions column to make changes.
- After your data appears in the menu, if there is an X or a question mark (?) beside a data source in the menu, manually review the data source to see whether you have that type of data in your environment.

Review MITRE ATT&CK tactics and techniques and find detections
As you review common cybersecurity attacks and threats, you might notice that most reports are providing common framework alignments such as the MITRE ATT&CK techniques used in the attack.
Follow these steps to search for these MITRE ATT&CK techniques in SSE to quickly see if your environment has detections to help protect against them:
- From the main menu in Splunk Security Essentials, navigate to the Security Content page.
- Copy and paste or enter one or more MITRE ATT&CK techniques from the attack report into the search bar. Alternatively, you can add and use the ATT&CK Technique filter to select the MITRE ATT&CK technique IDs you want to find content for.
- Review the detections that appear to determine if your environment is protected against the potential attack.
- (Optional) Click Edit and enable the Content Enabled filter and the Data Availability filter. Use the Content Enabled filter to filter the detections based on what detections are already running in your environment. If a detection is enabled, you already have some protection against the listed techniques. Use the Data Availability filter to filter the detections based on whether you have the data available for them.

The SSE security journey
No matter where you are in building out your security operations and processes, Splunk Security Essentials has a way to help you assess, implement and measure your progress. Using the SSE Security Data Journey, you can develop a maturity roadmap with security and data recommendations to secure your business. You can track the progress of your security program and understand milestones and possible challenges at each stage of the journey. You can also implement best practices and security detections with the data you’re already collecting to improve your security posture. Finally, you can use the data onboarding guides to collect and analyze additional host, network, and account activity.


