Suspicious session behavior
Working as part of a fraud detection team, you need to be able to quickly identify when a customer’s account is taken over by a fraudster.
Some types of session behaviour may indicate that fraud is occurring, for example, a string of actions taken by a user such as a failed login, followed by a successful login, then a profile edit, then money movement. This process walks you through how to find incidents like this.
Required data
Procedure
The information in this article applies to Splunk Enterprise Security (ES) versions 7.x. If you have upgraded to Splunk Enterprise Security version 8.x, some terminology and steps might not apply. For additional assistance on this use case with ES 8.x, Splunk Professional Services can help.
- Install and configure the Splunk App for Fraud Analytics, following the installation instructions.
- From the Incident Review tab in the top toolbar of Splunk Enterprise Security, sort by Risk Score and find an incident to investigate. Click on the caret to the left of the Incident Title to view the risk rules associated with the incident. In the example below, user libby_moribayed85 is selected. There is only one rule that contributed to the risk score total for this user that is listed as Suspicious Behavior. This behavior alone is enough to warrant a high risk score, so it should be investigated.
- Click on the Action caret then Click Here to Investigate.
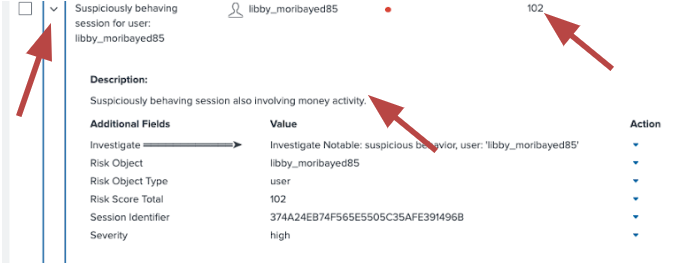
- This takes you to the Fraud Risk Exposure Analysis dashboard. Scroll down to the Detailed Investigation Link Analysis section, click on the user libby_moribayed85, then click a session_id.
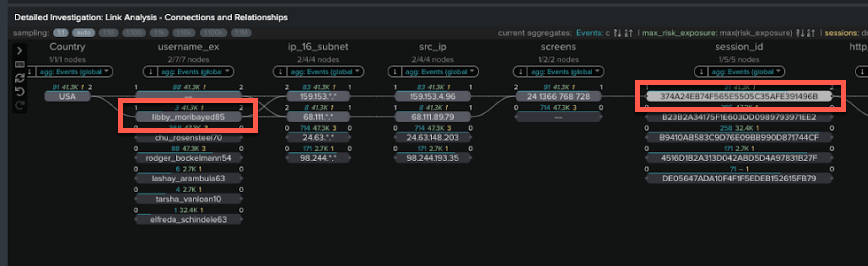
- To the right of this area you can then view a string of actions taken by this user - a failed login, followed by a successful login, then a profile edit, then money movement. This pattern of behavior is considered highly suspicious and is the basis for the “suspicious behavior” risk rule triggered in this example.
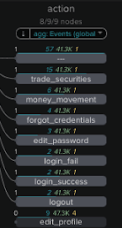
- Scrolling up to the Link Analysis panel you can see a number of graphs to show the timing for events, which can help you understand them better.
- Scrolling below the Link Analysis panel you can see a velocity analysis with the risk listed in a dollar amount. This is based on transactional data (not visible in the dashboard) relating to how much money was moved, and the risk calculated based on business risk. These panels expose other high risk user activities that may have occurred at the same time. Because fraudsters are usually not content with just a single victim and attack and they usually try many at one time, you can use this information to identify additional attempts.
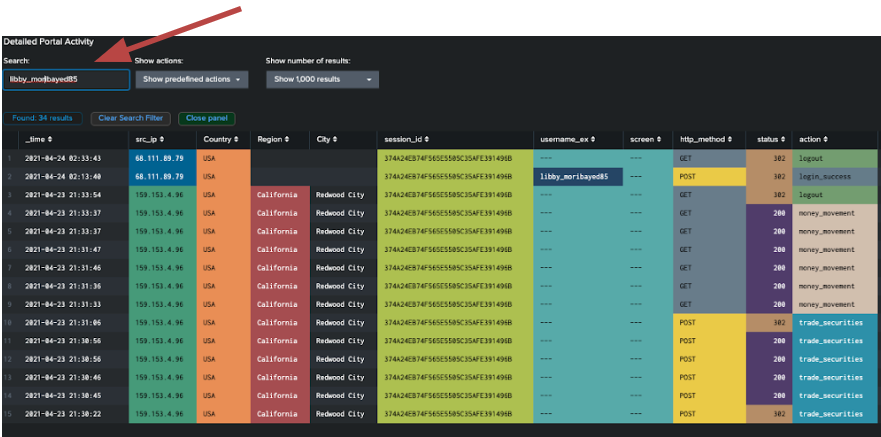
- Finally, if you want to see more detail on the behavior you've identified, you can scroll down to the Detailed Portal Activity panel and paste in the username of interest to get a view of the web logs.
Next steps
Now that you've completed this one, have a look at the other tutorials in the Detecting consumer bank account takeovers use case. In addition, this resource might help you understand and implement this guidance:

