Using the OT Security add-on for Splunk to ensure NERC CIP compliance
CIP scorecards and reports included in the OT Security Add-On for Splunk help automate and streamline NERC CIP compliance activities. Whenever possible, they leverage Splunk's Common Information Model (CIM) and rely on the asset framework in Splunk Enterprise Security to make implementation easier and faster for organizations.
All scorecards and reports are grouped together under CIP Numbers (for example, CIP-002, CIP-004, etc) to help quickly navigate between the various requirements; however, there are differences between the two that are important to understand when using them for reporting purposes.
Scorecards are a collection of CIP Requirements (R2, R4, etc.) for each area. They are not prefiltered for reporting purposes to auditors, but they allow organizations to understand their overall posture and state, as well as maximize flexibility when investigating potential issues.
Reports are more granular and designed to review and then hand over the results to an auditor. In addition, reports are pre-filtered based on the NERC CIP requirements and are designed to be used as input for an audit. Depending on an auditor's request, they might need additional filtering to answer specific queries, for example, requests for records regarding a specific asset or user.
Data required
How to use Splunk software for this use case
The following section breaks down the scorecards and reports by their major classifications:
NERC CIP 002
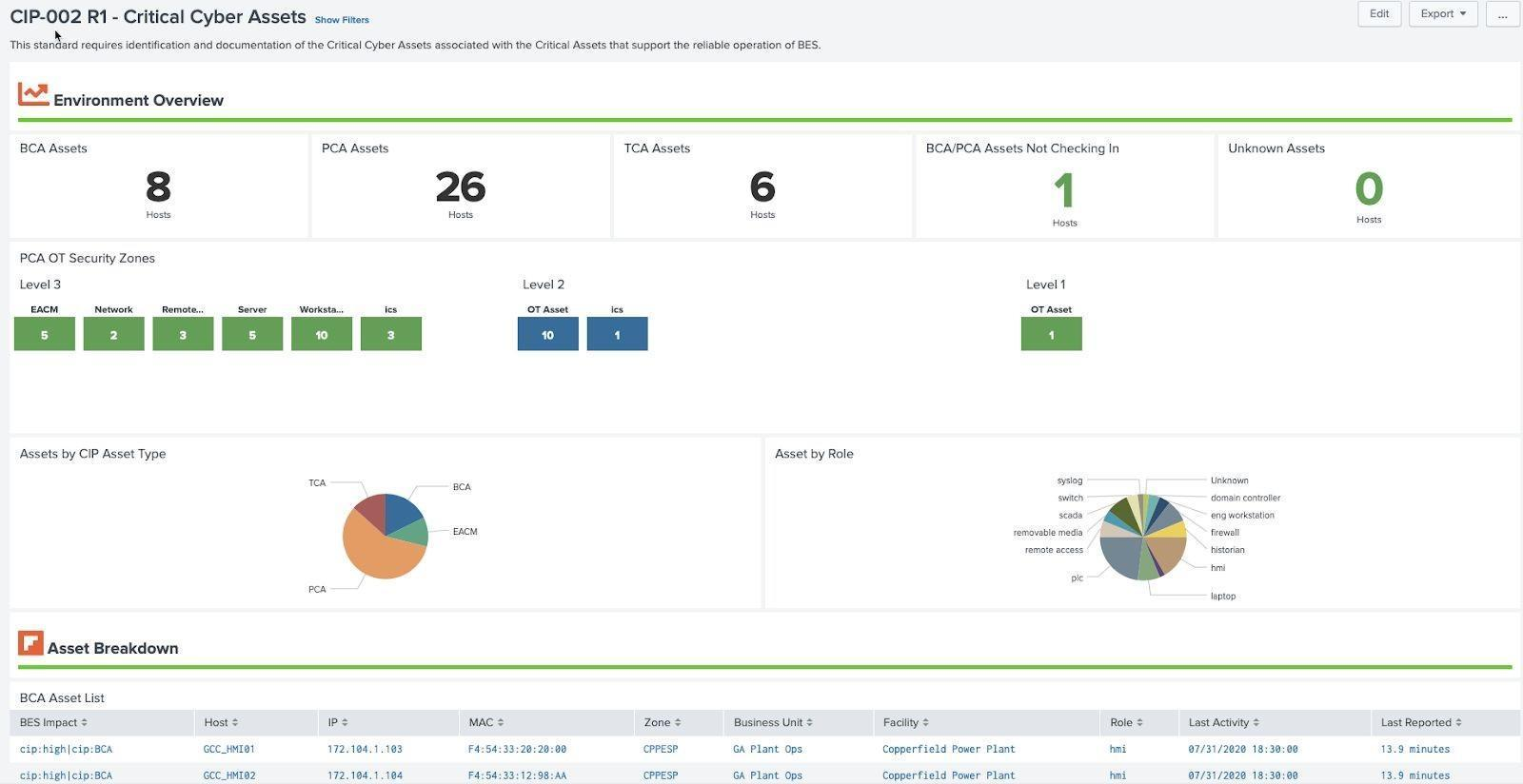
NERC CIP requires BES Cyber Systems to be classified and broken down by specific classifications and security zones. The classifications require an asset to be assigned a CIP criticality as well as CIP asset type. CIP explicitly defines criticality as Low, Medium, or High and has numerous asset types (BCA, PCA, EAP are all examples). In addition, typically at a site level, an asset will be assigned to a CIP asset zone, although Splunk does not explicitly make that mandatory. The Critical Cyber Asset Scorecard shows how assets are classified in their environment.
Example: Critical Cyber Assets (CIP 002 R1)
NERC CIP 004
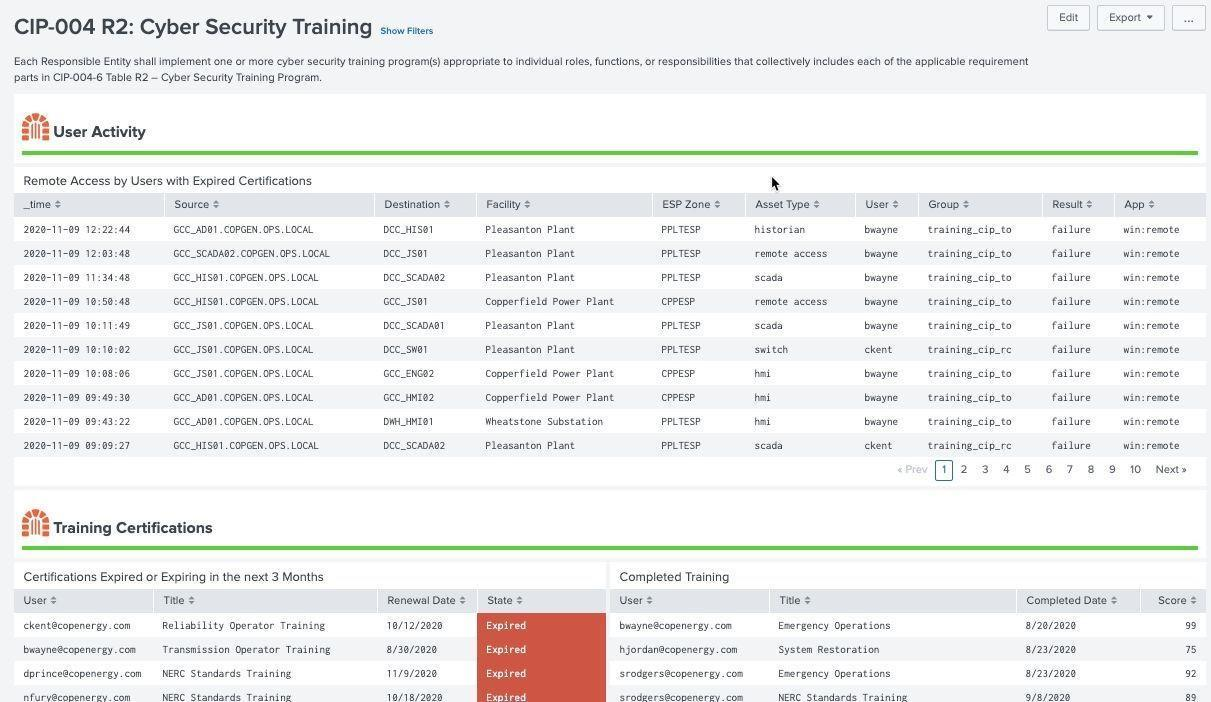
Individuals who access NERC CIP environments must be trained and certified before accessing assets remotely, onsite, or physically in that environment. NERC CIP requires that training requirements be tracked and monitored for expired certifications and then correlated with access records. This dashboard makes use of the authentication data model to determine remote or local access to systems by individuals required to be NERC CIP certified.
Example: Cyber Security Training (CIP 004 R2)
NERC CIP 007
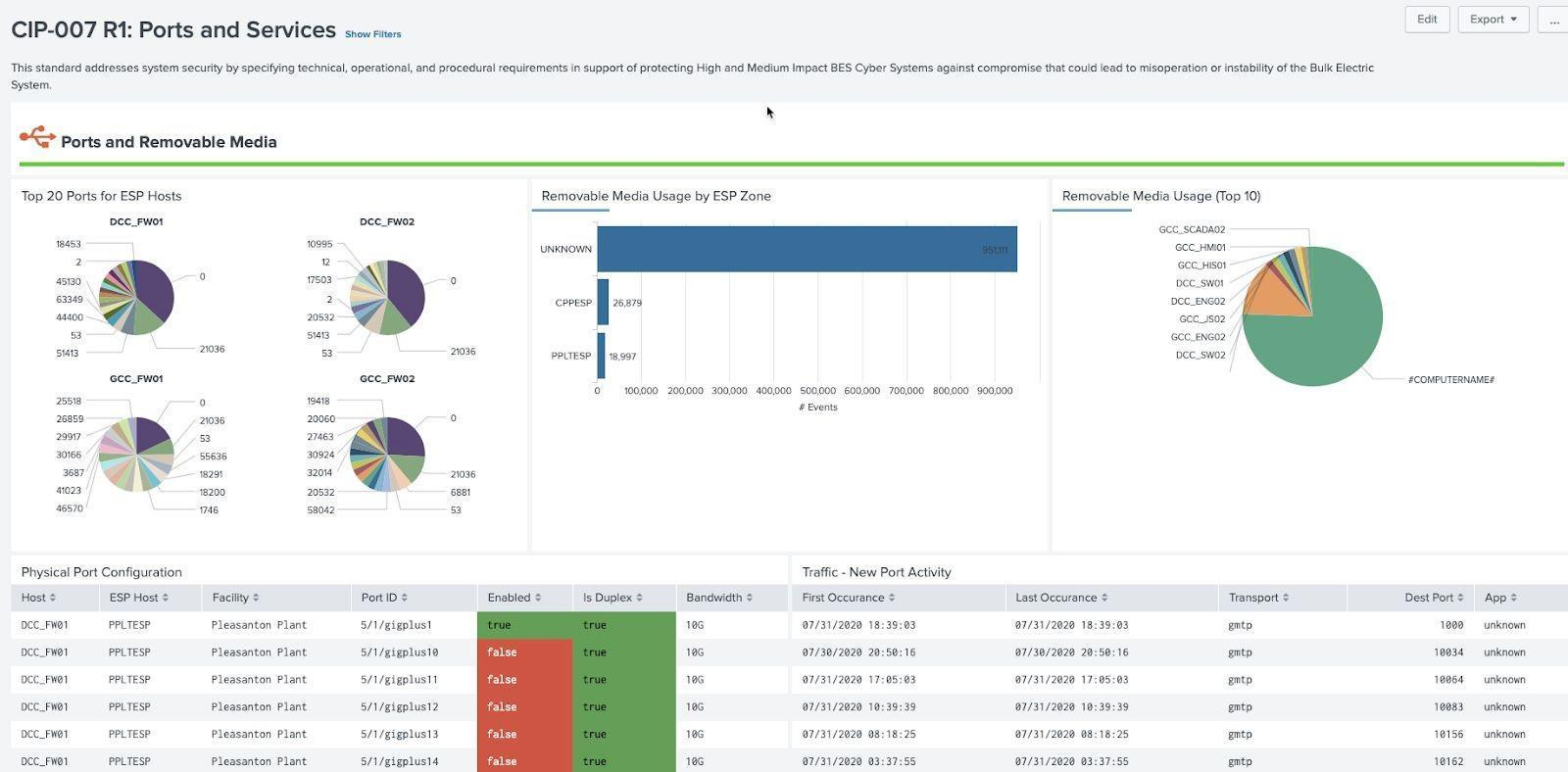
Ports and services present on machines is mandated by NERC CIP and involves many data sources relevant to these requirements. Firewall, routers, and switches can provide information on ports being used, as well as logs from machines themselves or data can be collected via Splunk Stream. In addition, events from endpoint protection logs that monitor USB usage, or directly from Windows events (current OS) as well as Windows registry (older operating systems) play a role in determining when remote media is being used. Because the source of remote media usage can vary, the macro get_removable_media_indexes can be used to point to specific indexes, sources, and source types that contain this information.
Example: Ports and Services (CIP 007 R1)
Next steps
Many more NERC CIP scorecards and reports are available in the OT Security Add-On for Splunk. In addition, these resources might help you understand and implement this guidance:

