Leveraging critical vulnerability insights for effective incident response
Organizations depend on Splunk to harness operational IT, OT, and Active Directory (AD) data to detect and respond quickly to threats. Without the ability to integrate critical vulnerability intelligence into the Splunk platform, security leaders are at risk of weakening incident investigations by not having full security context to take the right actions.
How to use Splunk software for this use case
The Tenable integrations with Splunk combine Tenable’s Exposure insights with the Splunk platform's correlation capabilities for complete visibility into all assets across the modern attack surface and their potential vulnerabilities, misconfigurations and unpatched components. With the combined solutions, organizations gain oversight in a unified threat detection, investigation and response analytics platform. Using Tenable and Splunk together enables joint customers to sync IT, Cloud, OT and AD vulnerability information, prioritize vulnerability remediation based on actual risk, request a remediation scan, and view the latest vulnerability summary for a machine during an investigation.
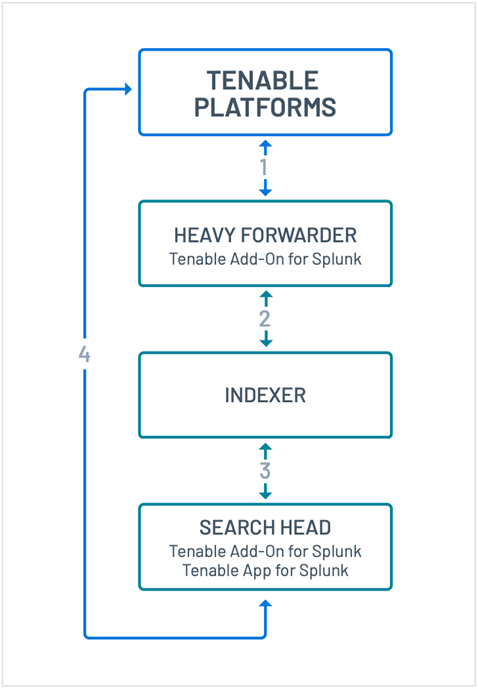
The integration works in the following way:
- All vulnerabilities are gathered from Tenable.
- Tenable data is indexed into the Splunk platform.
- Tenable data is searchable and reportable in default Splunk reports and the Tenable App for Splunk.
- Invoke Adaptive Response actions to enrich notable events.
When you have the Tenable integration for Splunk configured, you have the ability to:
- Discover additional hosts that were previously unknown to Splunk
- Enrich existing events with vulnerability context and state information
- Centralize vulnerability alerting and reporting
- Respond faster to the most critical vulnerabilities with Predictive Prioritization
- Utilize Adaptive Response Actions with Splunk Enterprise Security (optional)
- Sync vulnerability information, including state from Tenable platforms
- Prioritize remediation based on the likelihood of a vulnerability being exploited
- Scan a host during an investigation
- Request a remediation scan during an investigation (Tenable.sc)
- Get the latest vulnerability summary for a host during an investigation
- View a single dashboard with configured vulnerability feeds
Next steps
The following resources will help you get started with the Tenable integration for Splunk:
- Tenable Documentation: Tenable's Splunk Integration
- Tenable Demo Video: Splunk/Tenable Integration Demo
- Splunkbase: Tenable Add-on for Splunk, Tenable App for Splunk
- Tenable Support: https://community.tenable.com/s/
- Tenable Products: Tenable Vulnerability Management, Tenable Security Center, Tenable Cloud Security, Tenable Identity Exposure, Tenable OT Security
- Tenable Product Trial: Tenable Vulnerability Management
The user- and community-generated information, content, data, text, graphics, images, videos, documents and other materials made available on Splunk Lantern is Community Content as provided in the terms and conditions of the Splunk Website Terms of Use, and it should not be implied that Splunk warrants, recommends, endorses or approves of any of the Community Content, nor is Splunk responsible for the availability or accuracy of such. Splunk specifically disclaims any liability and any actions resulting from your use of any information provided on Splunk Lantern.

