Use Case Explorer for Security
Without the right strategy, security teams are flying blind. Suddenly, cyberattacks have the potential to grow into catastrophic events with serious ramifications for organizations both big and small. Even the largest, most profitable companies in the world have fallen victim to malware that might have been detected with a better, more unified solution.
To tackle threats that loom large, the answer is to become digitally resilient. By starting or stepping up your organization’s security practice and preparedness — progressing through each stage of the journey depending on level of maturity and needs — you can better prepare for all manner of threats, attacks, compromises and other adverse events. Splunk's Use Case Explorer for Security is designed to help organizations become increasingly resilient as they expand into new cases:
- Security monitoring, incident management and compliance
- Enhanced alerting with threat intelligence and risk-based alerting
- Automation with security orchestration, automation and response
- Unified security operations
With the right tools, capabilities, and know-how, security teams are well positioned to monitor, detect, and respond to events before it’s too late. Threat detection and response happen faster with the Splunk Security suite of products:
Splunk Enterprise Security, Splunk Security Essentials, Splunk User Behavior Analytics, Splunk Threat Intelligence Management, Splunk Mission Control, Splunk Edge Processor, and Splunk SOAR.
If you're a user of Splunk Enterprise or Splunk Cloud Platform, this content can still help you understand the maturity journey ahead of you. You can find use cases that apply to these products in our library of Use Cases for Security with Splunk Platform.
| Use Case Explorer for Security | |||
|---|---|---|---|
|
|
|||
 |
 |
 |
 |
Is this your first time using the Use Case Explorer for Security?
- ►Click here to learn how to use it.
-
Learning how to use the Use Case Explorer is important to help you successfully get started and to get the most out of your Splunk Security solution, as well as help you see incremental value when incorporating additional solutions. The following video provides a brief but informative overview of the three use case explorers in Lantern: Platform, Security, and Observability. Wherever you are in your resilience journey and whatever use cases you need to accomplish, the content in the explorers can help.
The Value Realization Cycle
Now that you know how this Use Case Explorer and help, to use it effectively, you'll need to implement and follow a Value Realization Cycle within your organization. Two tools within the Use Case Explorer will help you do this - the Explorer Map and the Use Case Registry.
The Value Realization Cycle is a continuous process for identifying, implementing, and evaluating the value of new use cases that your business adopts.
In order to get maximum value out of your investment in Splunk security products, it's vital to intentionally put a Value Realization Cycle in place. We recommend that your organization establishes a use case planning session at least every other month to ideate and refresh new use cases to be deployed.
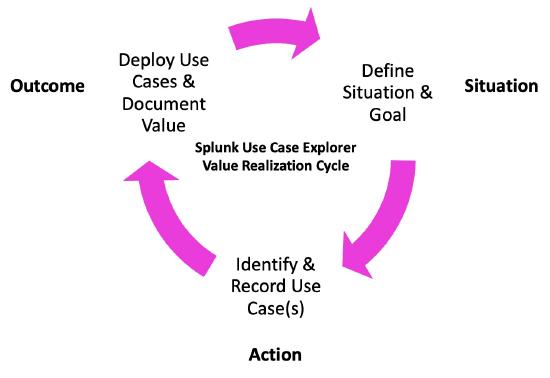
The Value Realization Cycle consist of a few different steps:
- Step 1 - Define a situation and goal. This can be a very targeted tactical challenge or a more expansive one. For example, you might aim to reduce the mean-time-to-detect (MTTD) of security-related incidents or to automate your incident response.
- Step 2 - Identify and record use cases. There could be one or more use cases that help you improve the situation and achieve the goal you defined in step 1. For example, you might wish to enrich the quality of alerts, or you might have a separate use case for adding threat intelligence feeds. Use the Explorer Map to help you identify use cases you can apply.
- Step 3 - Deploy use case(s) and document the value achieved. Use the Registry to help you track and document your progress.
And then, repeat!
The Explorer Map
The Explorer map is a high-level planning guide to ensure you are targeting all areas of security for your business or mission. You can see the map at the top of this page. Click into the map's workflow stages (Foundation Visibility, Prioritized Actions, Proactive Actions, and Optimized Experiences), and then the focal areas within each. You'll find use cases and best-practice guidance within each of these focal areas which you can start to apply right away.
You can track your progress in achieving use cases with the Use Case Registry.
The Use Case Registry
The Use Case Registry is a tool used to track the specific use cases you want to deploy, along with the names of use case implementation owners and timelines for completion.
As well as running a regular use case planning session at least every other month, we recommend that you have weekly or bi-weekly team meetings focused on the Use Case Registry to checkpoint and track your progress in achieving the value you've identified from the use cases you choose to implement.
You can create the Use Case Registry in a spreadsheet or project management tool of your choice. Here is an example of a Use Case Registry you can use, or you can download this template file. You might want to add extra columns to these examples to track additional information such as status, prerequisites, or comments.
Use Case Product Expected Value Owner Target Date Onboarding data to Splunk Enterprise Security Splunk Enterprise Security
Identify, ingest and centralize visibility for essential security, infrastructure and application data
Steve Striker
<date>
Monitoring for indicators of ransomware attacks with Splunk Enterprise Security
Splunk Security Essentials
Grow security maturity using expanded use cases and content addressing current and emerging threats
Kenny Powers
<date> Implementing RBA in Enterprise Security
Splunk Enterprise Security
Reduce alert footprint and identify slow evolving threats
Stacy Rai
<date> Using Splunk Enterprise Security to ensure GDPR compliance Splunk Enterprise Security
Achieve GDPR Compliance
William White
<date>

