Using the Splunk security suite for incident response management
Incident response activities are normally a massive team effort that involves coordination on many levels. An incident commander must have the tools, processes, and people to solve the complex problems involved in a potential breach, and do so in a timely manner. Keeping track of all incident management tasks in a single pane of glass is essential to ensure that incidents can be handled effectively and successfully. Since incident commanders rely upon the most up-to-date information available, it's important to understand how information is gathered for viewing in a single pane of glass. Splunk Enterprise Security, Splunk Mission Control, and Splunk SOAR work together to provide this unified view.
The security team has declared an incident, now what?
During incidents, the commander, who leads the activities surrounding the incident, has several responsibilities to ensure a successful response. Splunk Mission Control distills this information into one page and is crucial for the commander's success, especially since time is short. Splunk Mission Control displays all information relating to the incident in a single dashboard, and capabilities to let the commander take additional actions, such as running playbooks, from this single point. The commander also has access to incident review, investigations, the threat intelligence features of Splunk Enterprise Security, and the response and playbook features of Splunk SOAR, all from within the Splunk Mission Control dashboard.
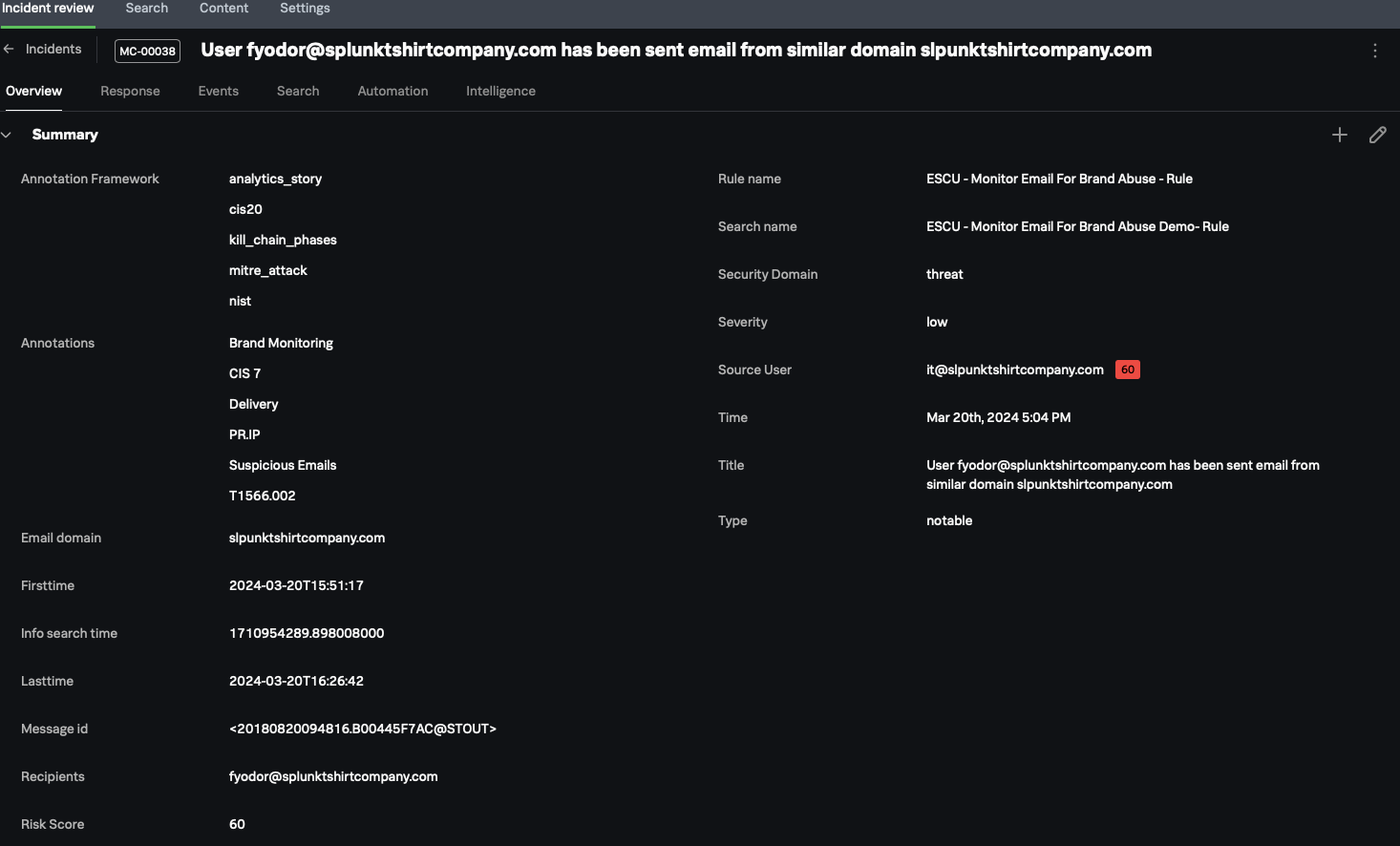
In the Splunk Mission Control Incident review screen, the Overview tab (shown below) contains detailed information about the incident. For example, the Annotation Framework section shows information about the nature of the incident, and the Annotations section shows detailed contextual information, which helps with narrowing down the nature of the threat.
The commander can access additional information by selecting one of the other tabs at the top of the screen, for example:
- The Response tab shows response templates.
- The Events tab shows the actual events that contain all supporting information related for the incident.
- The Search tab is useful if you need to run a search without the need to leave the incident.
- The Automation tab shows automation results, such as actions or playbooks.
- The Intelligence tab shows the threat intelligence feed associated with the incident.
Managing the incident
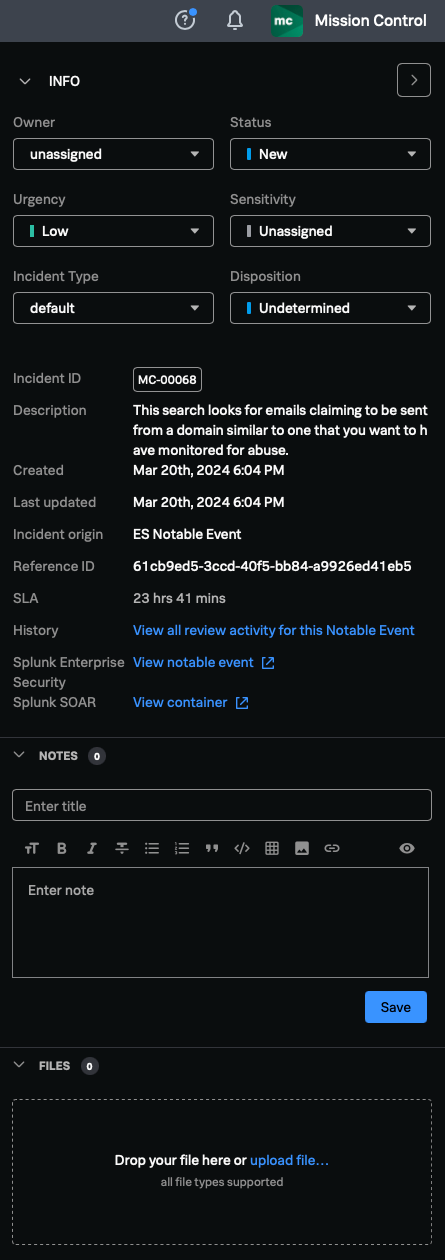
After an investigation starts, the commander can review the current status of each incident and determine if it needs further enrichment. In the Incident review screen shown above, the INFO section to the right-hand side allows the commander to change the incident's status, urgency, incident type, etc. Finally, the commander can add additional information, such as notes or files, to the event, or access the Splunk Enterprise Security notable event or Splunk SOAR container from this view.
Next steps
These resources might help you understand and implement this guidance: