Configuring the Universal Correlation Search to create notable events
You have integrated your Splunk Observability Cloud alerts with Splunk Cloud Platform or Splunk Enterprise and normalized Splunk Observability Cloud alerts into the ITSI Universal Alert Schema. Now, using the Content Pack for ITSI Monitoring and Alerting, you want to configure a Universal Correlation Search to create notable events in Splunk ITSI.
Solution
The diagram below shows the overarching architecture for the integration that's described in Managing the lifecycle of an alert: from detection to remediation. The scope for this article is surrounded by the pink box in the diagram.
The Universal Correlation Search in the Content Pack for ITSI Monitoring and Alerting finds the alerts which are stored in your Alerts index and normalized as Universal Alerts, and onboards them as notable events. These are stored in an index called ITSI_Notable_Event.
Procedure
- If you haven't already, download this ITSI Backup file and use the ITSI Backup/Restore utility to restore the correlation search "Universal Correlation Search - o11y" into your instance of Splunk ITSI.
- On the Correlation Searches page, find "Universal Correlation Search - o11y" and click it.
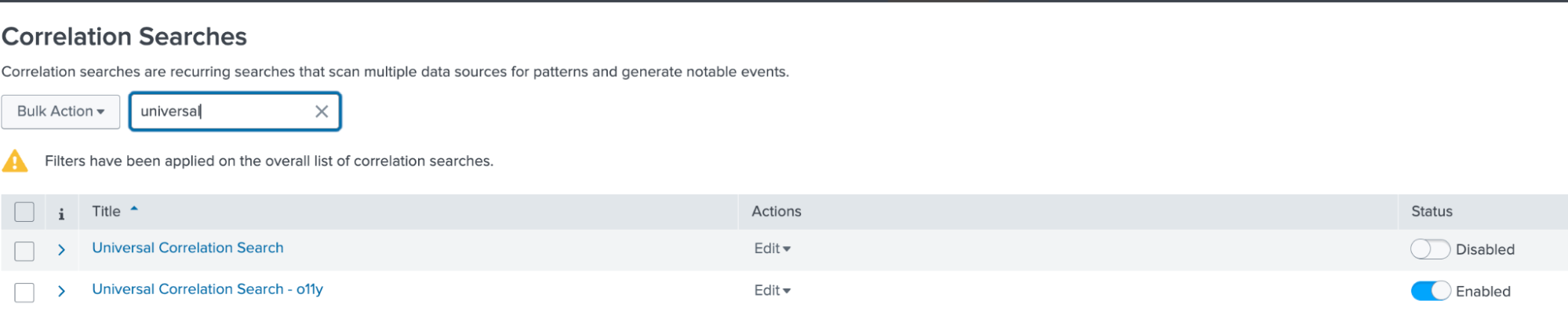
- Review the correlation search "Universal Correlation Search - o11y". This is a clone of the content pack correlation search called "Universal Correlation Search". A best practice is to clone the correlation search and make notes indicating the version cloned and any changes that were made. The correlation search has been modified to accommodate this integration. The correlation searches shipped with the content pack are considered a framework and can be used as in this case to develop a specific event analytics solution.
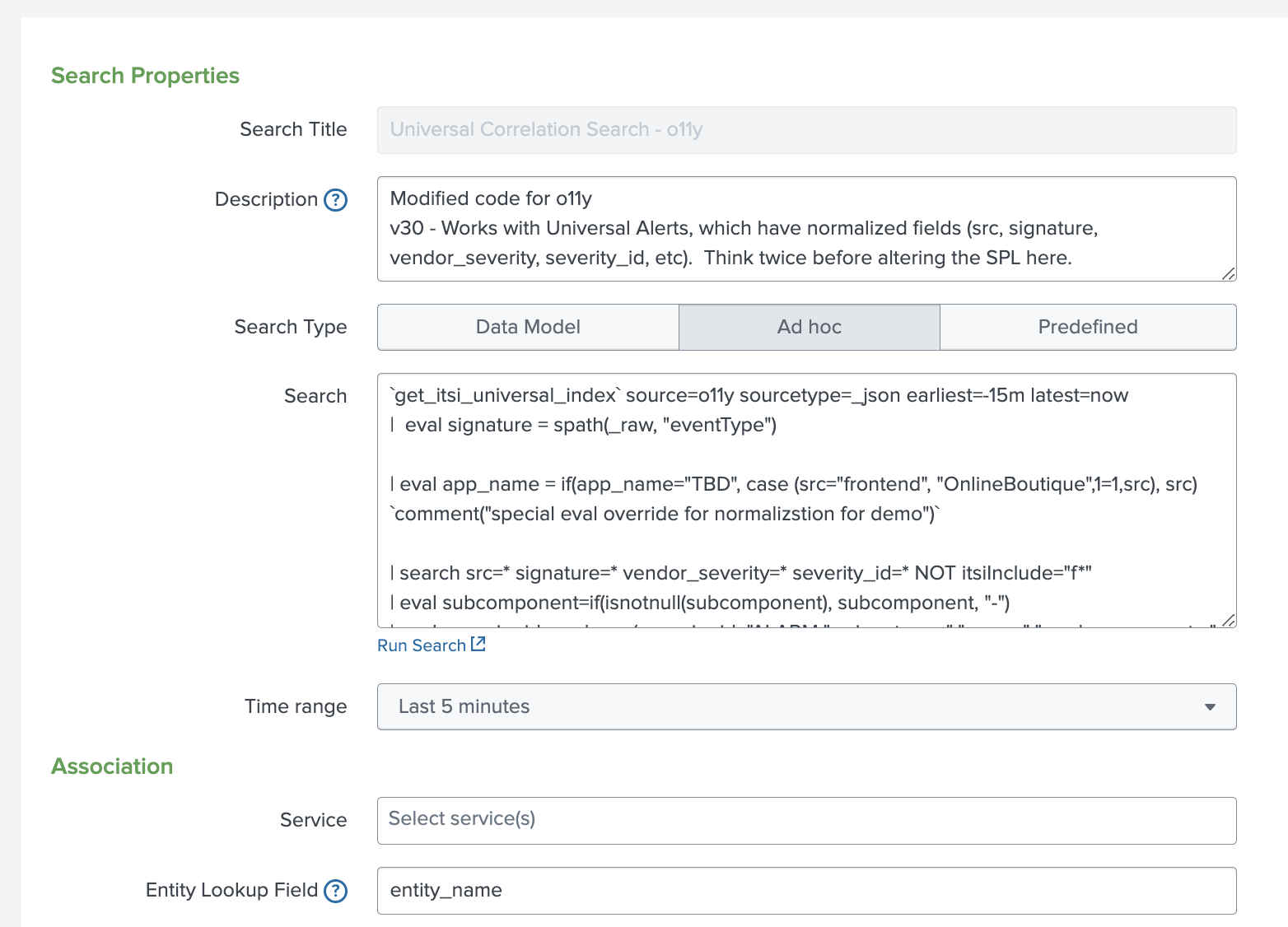
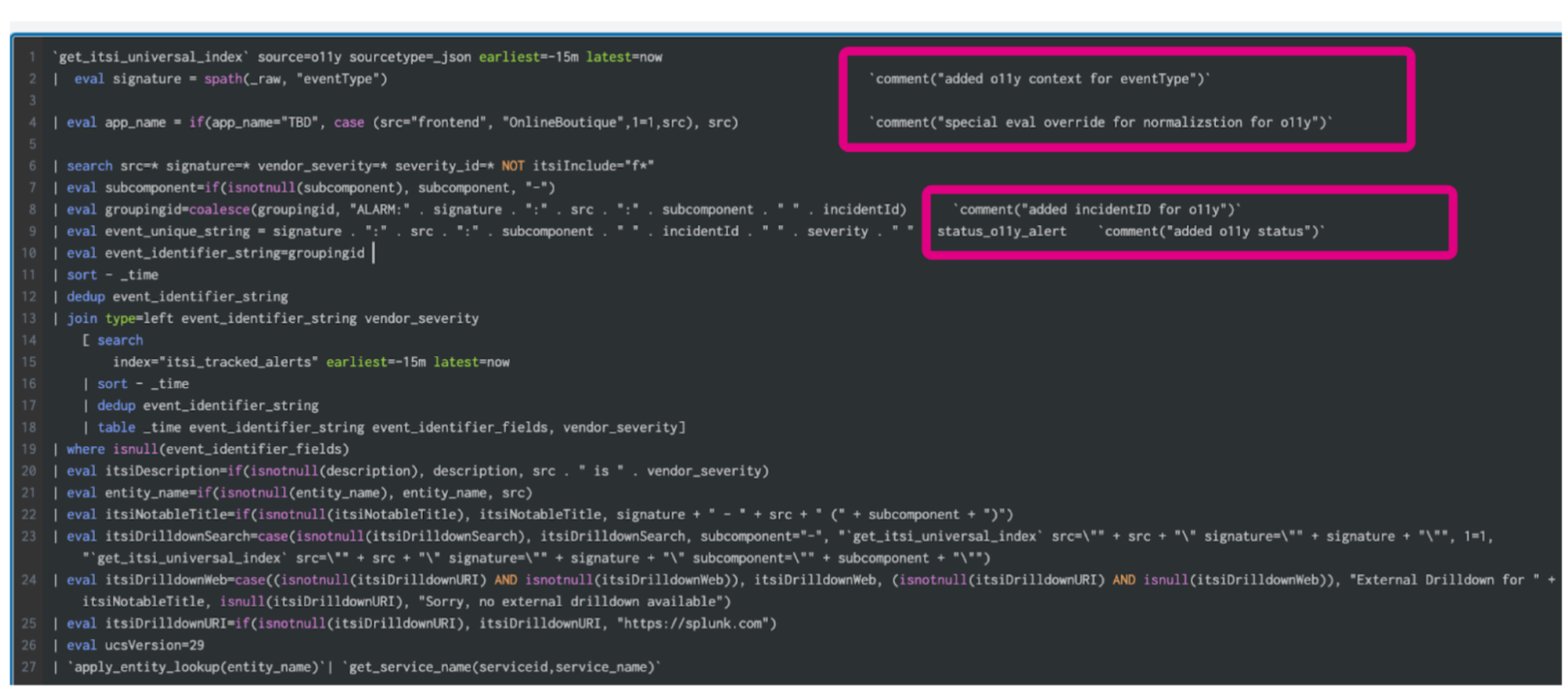
Note in the correlation search code below, comments have been added to highlight the modifications made for the Splunk Observability Cloud alert integration solution. The output of this correlation search are notable events that have been normalized to execute within the framework of the Content Pack for ITSI Monitoring and Alerting.
Next steps
Now that you’ve successfully configured a correlation search to create normalized notable events from the alerts you've configured to come in from Splunk Observability Cloud, continue to the next article to learn how to Configure the ITSI Notable Event Aggregation Policy (NEAP).
Still having trouble? Splunk has many resources available to help get you back on track.
- Splunk Answers: Ask your question to the Splunk Community, which has provided over 50,000 user solutions to date.
- Splunk Customer Support: Contact Splunk to discuss your environment and receive customer support.
- Splunk Observability Training Courses: Comprehensive Splunk training to fully unlock the power of Splunk Observability Cloud.
-

