Law enforcement active investigations
During active police investigations, the detectives and analysts on the case want to conduct digital forensics with the utmost care to ensure that no digital pieces of evidence that are gathered are thrown out in court due to mishandling.
Required data
- Criminal record data
- Driver's license and vehicle registration data
- Cell tower data
- CCTV camera data
- Email data
Procedure
The following searches are guidelines intended to help you get started. Depending on your data set, you may need to change field names or parameters. You can optimize the searches by specifying a time range.
Before you have a suspect, searching your database of known suspects can help you filter down to potential suspects based on key characteristics.
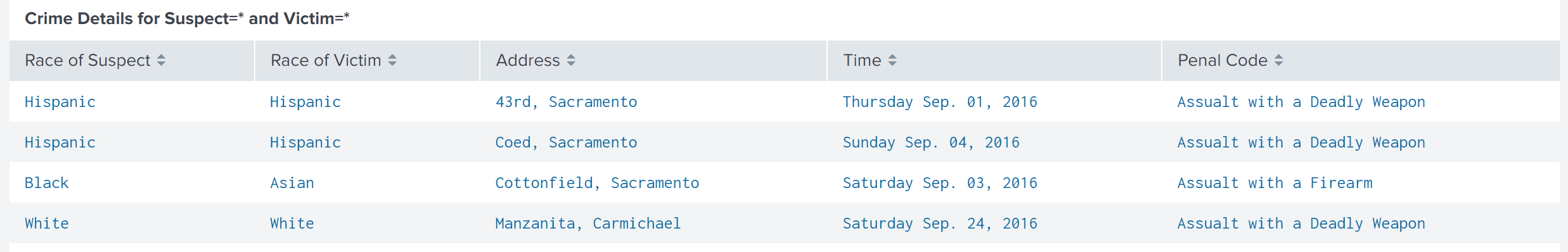
index=law_enforcement ROS=* ROV=* Address!=NULL | eval Time=strftime(_time, "%A %b. %d, %Y") | table ROS, ROV, Address, Time, PenalCode | rename ROS AS "Race of Suspect", ROV AS "Race of Victim", MonthName AS Month, PenalCode AS "Penal Code"
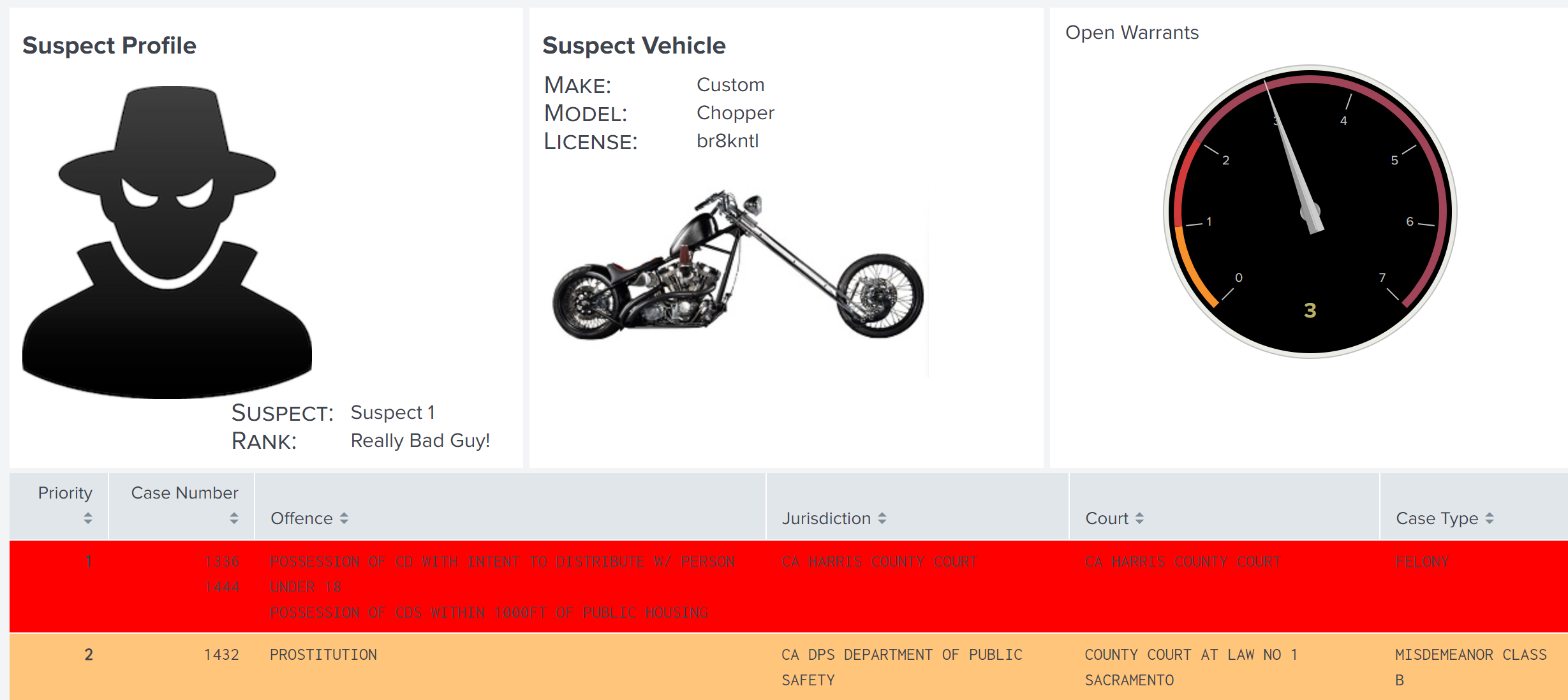
If you have identified a suspect and key data about that person, such as the vehicle they drive and the license plate number, you aggregate other information about that suspect and see all the information in a single, convenient dashboard. For example, you might want to see the number of open warrants a suspect has and what priority level those warrants are, which can help in determine how those warrants can be leveraged to the advantage of the investigation.
| inputlookup criminal_records.csv
| search Suspect="Suspect 1"
| stats values("Case Number") AS "Case Number", values(Offence) AS Offence, values(Jurisdiction) AS Jurisdiction, values(Court) AS Court, values("Case Type") AS "Case Type", BY Priority
For help creating dashboards, try the Splunk Dashboard Studio Examples Hub or see the dashboard documentation for Splunk Enterprise or Splunk Cloud Platform.
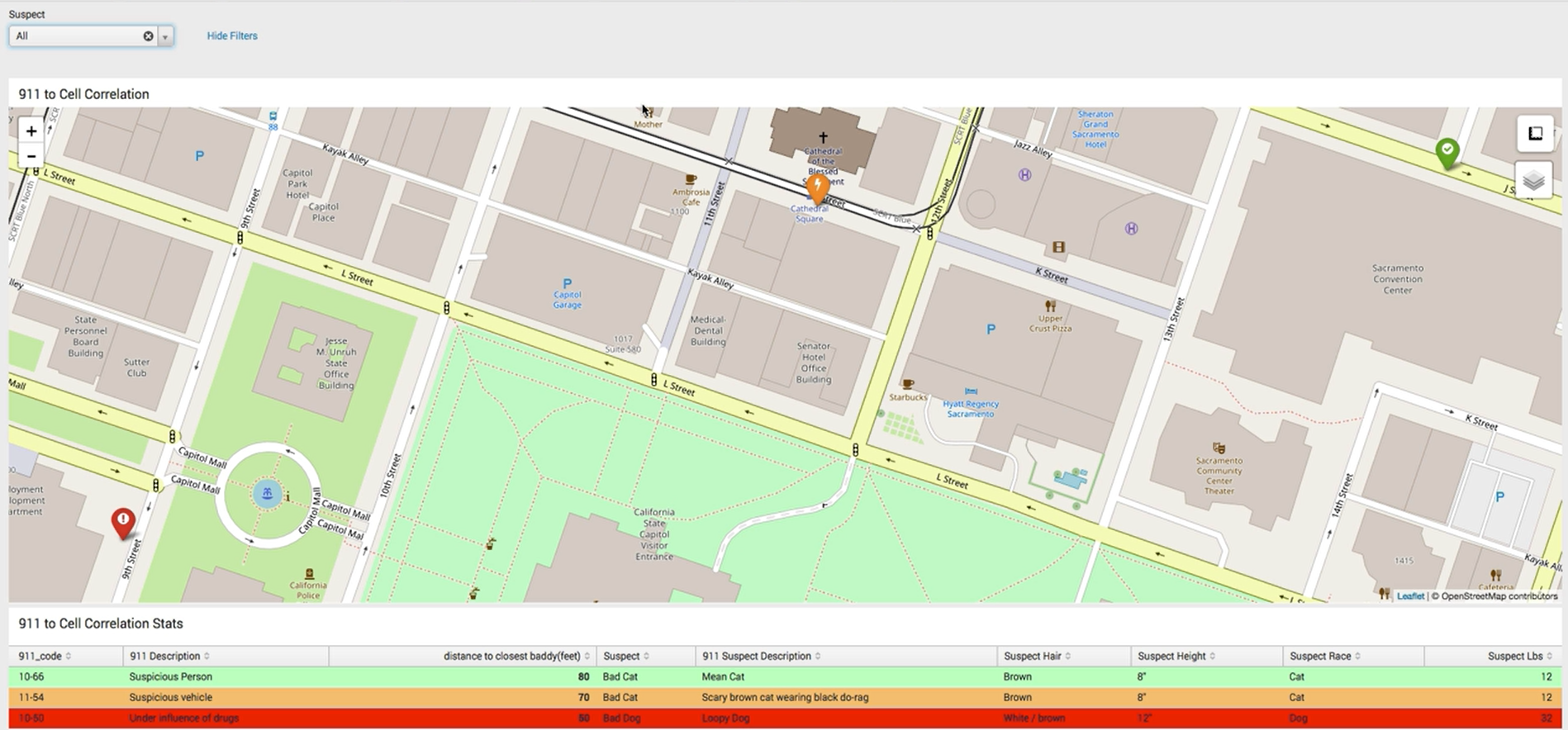
You might also be able to add the suspect's cell tower data to the same dashboard, which can help pinpoint the suspect's location at the time of a crime. You can drill into a suspect's cell tower data using geographical visualization to triangulate their location.
The victim's cell tower location data can also be helpful because data shows that suspects are often only 50 to 80 feet from the location of a 911 call for help.
| inputlookup baddy_to_911.csv
| search Suspect = "*"
| rename "distance to closest baddy(feet)" AS distance
| eval distance_to_911_call = case('distance' <=51, "Close", 'distance' >51 AND 'distance' <=71, "Average", 'distance' >=71, "Far")
| sort "distance"
| eval markerColor = case(like(distance_to_911_call, "%Close%"), "red", like(distance_to_911_call, "%Average%"), "orange", like(distance_to_911_call, "%Far%"), "green")
| eval icon = case(like(distance_to_911_call, "%Close%"), "exclamation-circle", like(distance_to_911_call, "%Average%"), "flash", like(distance_to_911_call, "%Far%"), "check-circle")
| eval description = "<b>"."Suspect Description: ".Suspect_Description."</b><br>"."Suspect Race: ".Suspect_Race."<br>"."Suspect Height: ".Suspect_Height."<br>"."Suspect Weight: ".Suspect_Weight_Lbs."<br>"."Distance (in feet): ".distance
| where distance_to_911_call="Close" OR distance_to_911_call="Average" OR distance_to_911_call="Far"
Even if the call came in some time after the crime, that location data can help you track down which security camera might have helpful footage. Then use camera data to quickly find which camera footage to investigate.
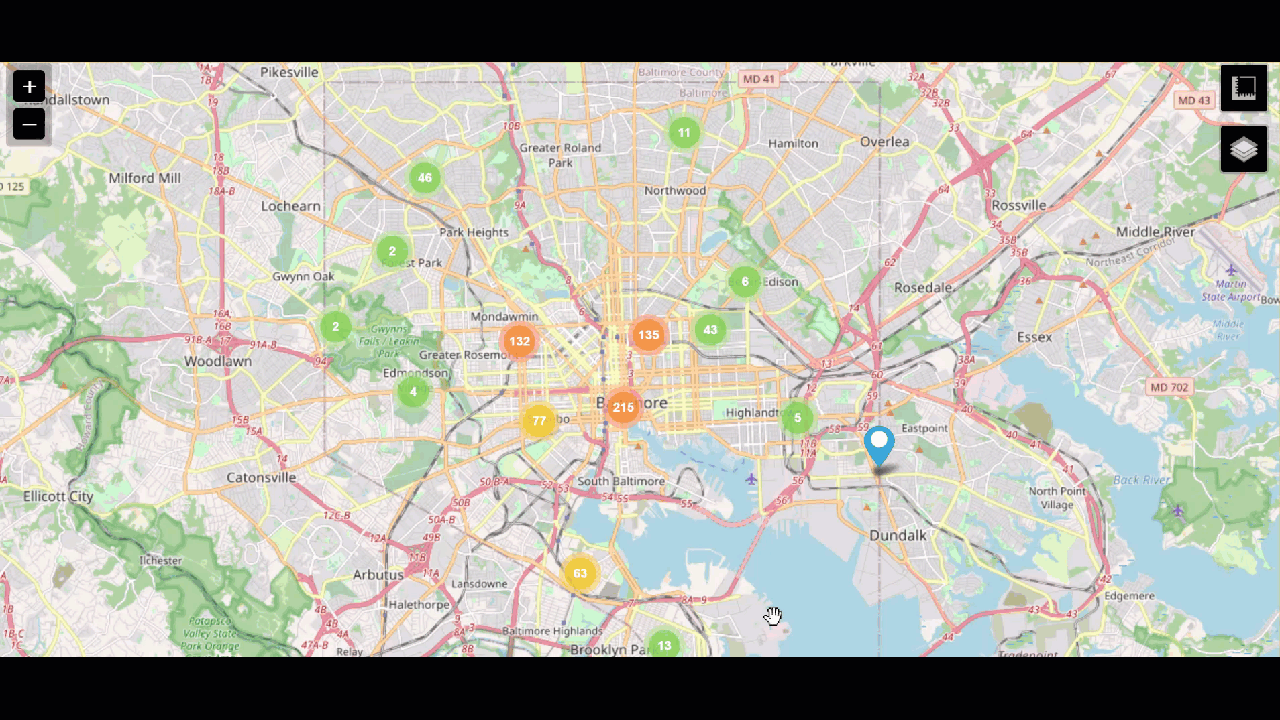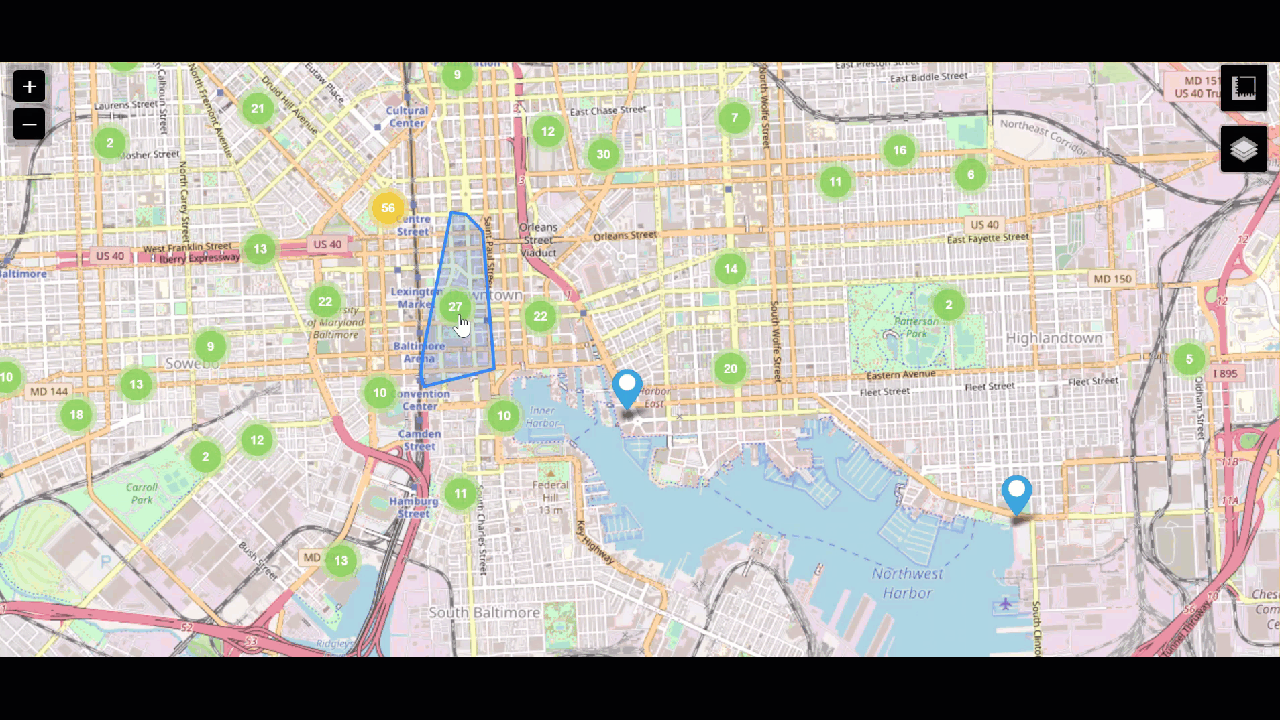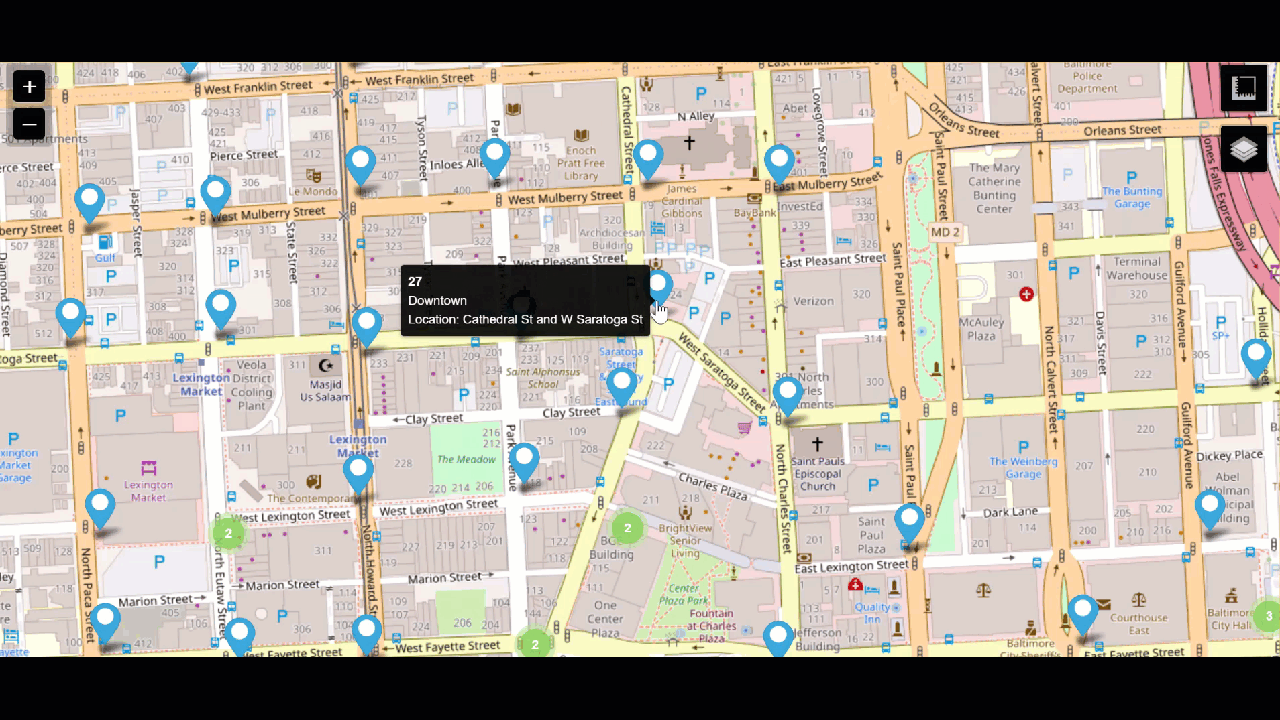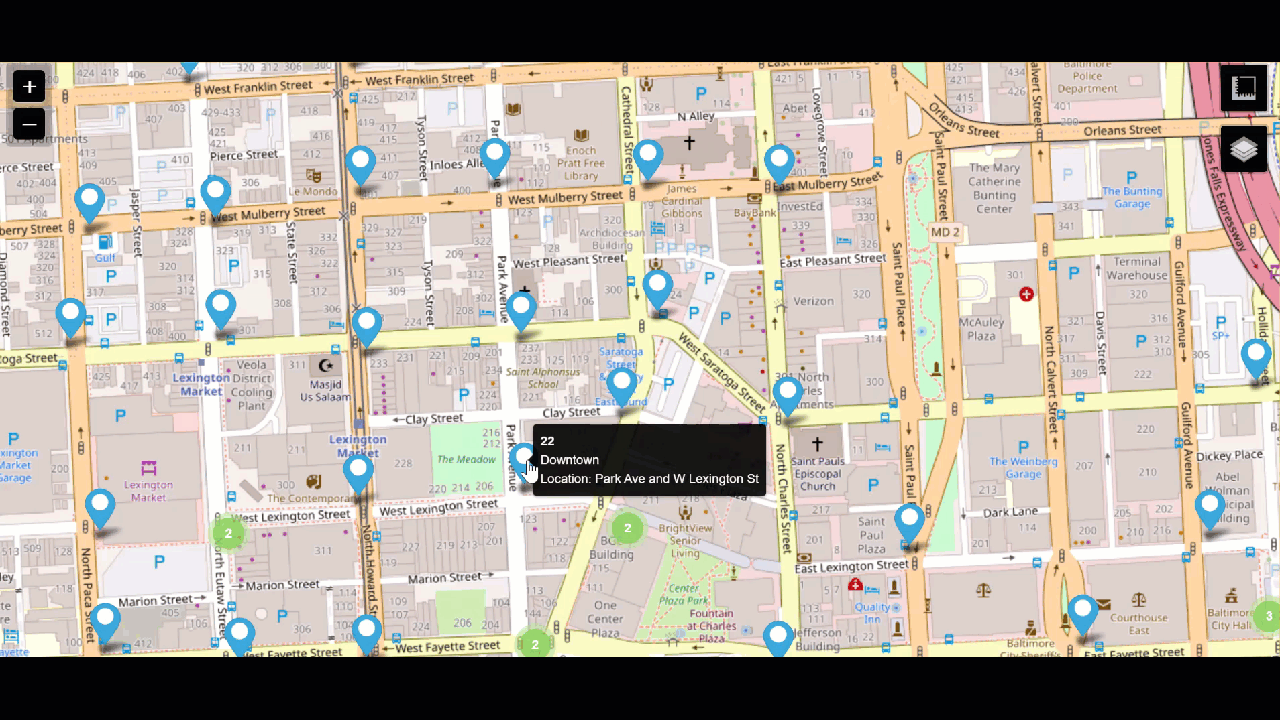
When you search a suspect's house and seize property, such as cell phones and cameras, the data from those devices can also be added to the Splunk platform. Email data can be cumbersome to sift through because it can span weeks or months or hundreds of thousands of emails across multiple suspects and victims. The Splunk platform can analyze addresses and language patterns to help you identify the emails that are most important in a small fraction of the time a human analyst could.
source="kimberlysdozier@gmail.com.Gmail.Content.2.mbox" host="gmail" index="test_email" sourcetype="gmail-mbox" | stats count BY from to
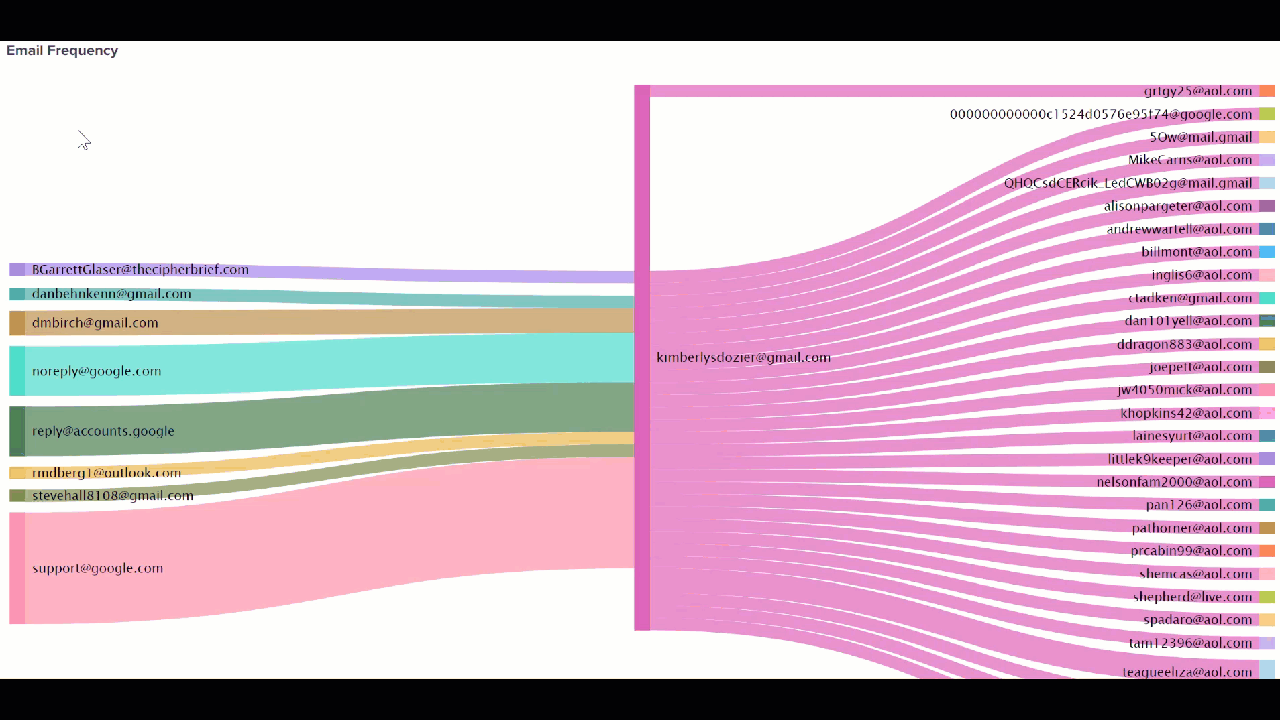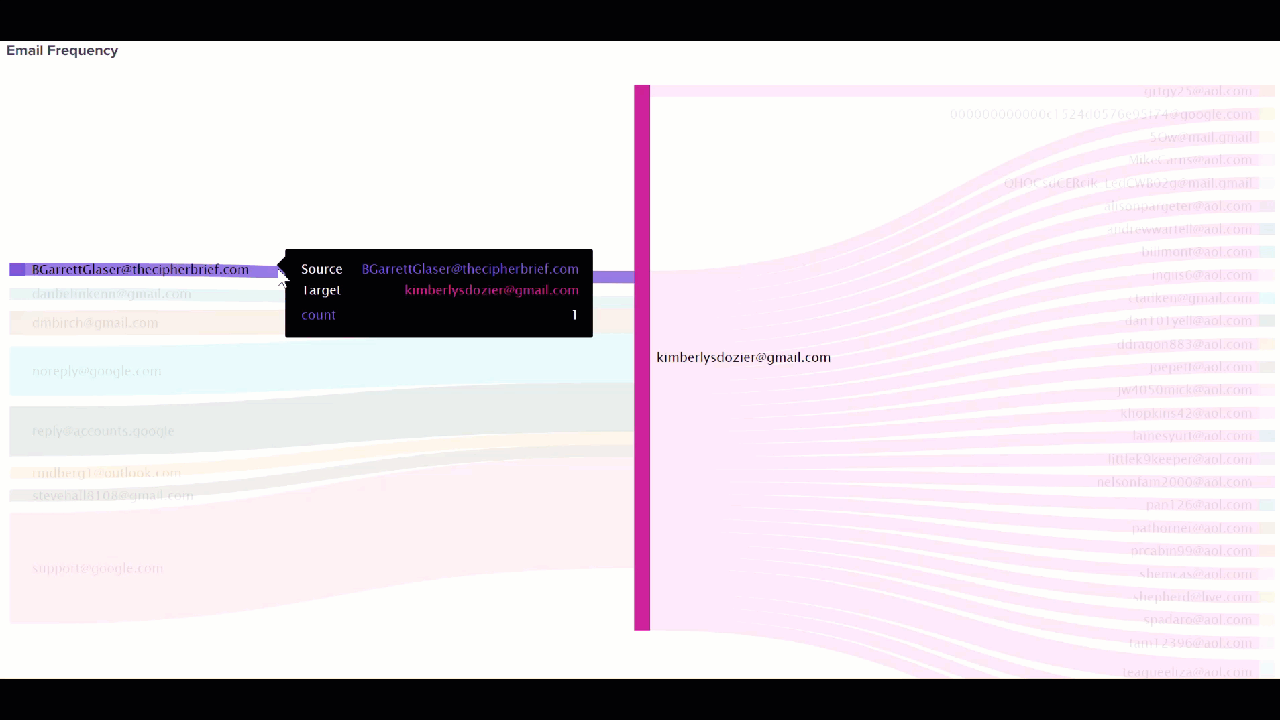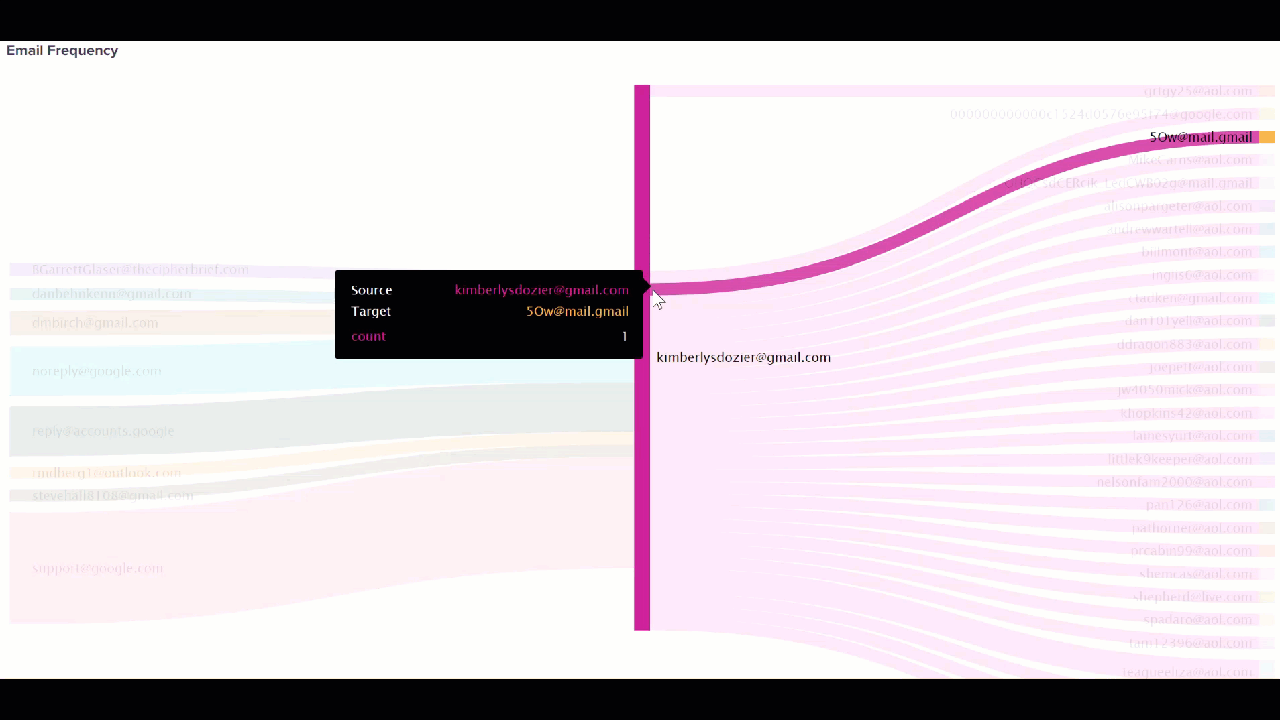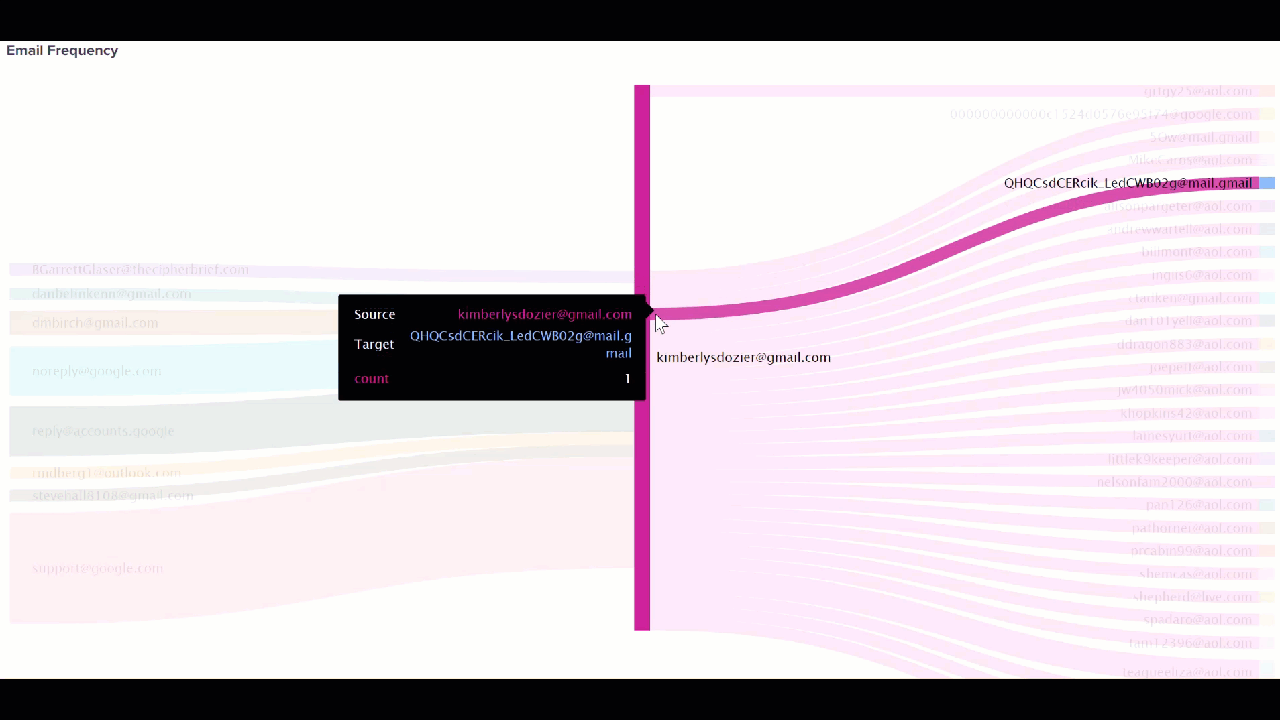
Next steps
Finally, you might be interested in other processes associated with the building a data-driven law enforcement strategy use case.

